ASSP professional spam
filter
|
( notes, articles, post installation
FAQs and suppport ) |
|
|
|
 |
How to
receive support
.
#013
|
What is
ASSP : "ASSP"
is the Anti Spam Smtp Proxy
server which includes the ASSP Web interface (GUI).
What is
ASSP Deluxe for cPanel : "ASSP Deluxe for
cPanel" is the ASSP frontend/integration for cPanel
; it's a set of php
scripts which allow to use/install/configure/execute/monitor ASSP on your cPanel server.
ASSP Deluxe for
cPanel includes features such as ASSP WHM interface, spambox
IMAP, email queue
finder, spam outgoing notifications, clamAV
unofficial signatures automatic updates, Daily
blocked email report, cPanel ASSP frontend for your
customers, ASSP SSL SNI and ASSP MySQL automatic
setup, ASSP Perl module automatic installation and other
features.
DO NOT ask "ASSP" or "ASSP Deluxe for cPanel"
support to cPanel support or to your isp/datacenter, they CANNOT
help you
. If your question is strictly related to "ASSP Deluxe for
cPanel" , please be sure you read first the FAQs on this page and be sure you have applied the
post
installation steps below; check also the
changelog and be sure your software
is all updated. If your problem is still
not fixed send an email
>>
HERE
<< . All
the support requests sent via email
which does not contain your server
licensed ip are ignored . Support
requests are worked in 24/48 hours, if you have an urgent problem and you can't
wait , you can disable temporarly ASSP following
these simple steps (there is
no need to uninstall ASSP if you have a problem which you can't
solve). ASSP Deluxe support does
not provide root support, if you need a
root investigation of your ASSP installation you may
order
this service or ASSP managed services
here . If you would report a
bug/idea/suggestion/feedback
related with ASSP Deluxe for cPanel please send an email
here.
skip_
If your question is
strictly related to "ASSP" and
ASSP Web Interface usage
(and not the ASSP Deluxe
for cPanel
frontend) you can
find an answer reading the
ASSP forum
and/or
the
ASSP mailing list or the
ASSP WIKI. If you would contact
ASSP forum
and/or the
ASSP mailing list report
ONLY your ASSP version , please remember that the ASSP community has no idea about cPanel
and/or
"ASSP Deluxe for cPanel" frontend.
DO NOT ASK "ASSP Deluxe for cPanel"
support in the ASSP forums or mailing list, they CANNOT HELP you,
you may ask only ASSP specific questions.
|
|
If you need professional email managed
services for your server please
look here (ASSP/email managed services) .
|
|
|
If you need root investigation of your
ASSP installation you can order
this service |
|
|
If
you would rate ASSP
Deluxe for cPanel please
click here
, thank
you. |
|
|
|
 |
cPanel
76 update :
76
If
your ASSP WHM interface is not
working after cPanel 76 upgrade please
follow this
# cd
/usr/local/cpanel/whostmgr/docroot/cgi
# wget -r -nH --cut-dirs=10
http://www.grscripts.com/asspwhm/whm.tar.gz
# tar xvzf whm.tar.gz;rm -f whm.tar.gz
# cd /usr/local/assp/deluxe
# wget -r -nH --cut-dirs=10
http://www.grscripts.com/assp150/deluxe/assp.tar.gz
# tar xvzf assp.tar.gz;rm -f
assp.tar.gz;chmod 755 *.*;chmod 755 *
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php
force=yes
Now open your ASSP WHM and
STOP and START
ASSP using ASSP WHM interface
If
your ASSP WHM interface is not
working and you have cPanel < 76 please
follow this
# cd
/usr/local/cpanel/whostmgr/docroot/cgi
# wget -r -nH --cut-dirs=10
http://www.grscripts.com/asspwhm/whm.tar.gz
# tar xvzf whm.tar.gz;rm -f whm.tar.gz
# cd /usr/local/assp/deluxe
# wget -r -nH --cut-dirs=10
http://www.grscripts.com/assp150/deluxe/assp.tar.gz
# tar xvzf assp.tar.gz;rm -f
assp.tar.gz;chmod 755 *.*;chmod 755 *
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/fix_ioncube.php
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php
force=yes
Now open your ASSP WHM and
STOP and START
ASSP using ASSP WHM interface
|
|
|
ASSP Deluxe for cPanel
post-installation steps
(
#16 )
It's
strongly recommended you
apply carefully following
steps right after the ASSP installation ;
these steps reduce issues to you (admin) and to your customers .
0) ASSP
(ASSP = Anti Spam Smtp Proxy) works like an smtp
proxy before EXIM ; each time you need to analyze a problem always
remember how works ASSP
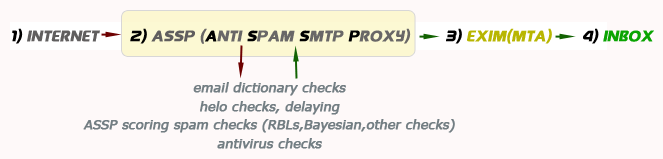
So, each time you need to analyze a blocked email problem first check if the
email was blocked by ASSP using commands like this
# grep "blocked_email"
/usr/local/assp/maillog.txt
# grep "ip_address" /usr/local/assp/maillog.txt
# grep "blocked_email" /usr/local/assp/maillog.txt
# grep "blocked_email" /usr/local/assp/maillog.txt | grep "spam found"
..
and , if the problem is not ASSP related check the EXIM
maillog using something like this
# grep "email" /var/log/exim_mainlog
You can monitor the ASSP log in this way
#
tail -f /usr/local/assp/maillog.txt
1) Open
your ASSP WHM INTERFACE and enable the
"ASSP SCORING MODE" .
Advantages :
- clients have only few SPAM filters on their
cPanel ASSP page , less confusion , easy of use
- better SPAM detection and reduced
false positives (
good email blocked ) .
Once you have enabled ASSP SCORING MODE
you may analyze what's happening on ASSP maillog
# tail -f /usr/local/assp/maillog.txt
Any "message ok" is a message accepted which will passed to
EXIM. Any
"[spam found]" is a message blocked by ASSP scoring mode, for
example ;
Example of a message blocked due to ASSP SCORING
[MessageScore]
Feb-29-12 02:47:09 id-33050-00951
[MessageScore] 13.16.3.5 <da@so.com> to: gm@ma.com [spam found][blocked] --
totalscore(58) over
MessageScoringUpperLimit -- [Make today YOUR lucky day
– join Ruby Rewards] ->
/usr/local/assp/spam/33050-00951.eml;
Example of a message passing the ASSP SCORING
[MessageOK]
Feb-25-12 09:13:09 id-33017-00873 [MessageOK]
27.1.1.20 <k@fin.com> to: mi@tw.com message ok
[my daily report];
Example of a message blocked due to invalid address
(no local filter) [InvalidAddress]
Feb-29-12 02:47:48 id-33050-00954
[InvalidAddress] 22.7.27.4 <ino@or.com> invalid address rejected:
wheeler@local.net;
If you activate the SPAMBOX (see the steps below) ALL the blocked
SPAM will
be collected in the client spambox . You can activate spambox below
at step 6)
2) By
default ASSP will be installed with moderate/relaxed antispam settings ;
current settings should be enough
to block more than 95% of all received spam ; in the first days of usage
some spam could pass however the risk to block a good email will be very
low.
If your users want set more relaxed or aggressive spam settings they
can do it using their ASSP Deluxe for cPanel frontend.
cPanel (port
2082 or https 2083) > ASSP icon > SPAM Scoring
Especially in the first days of usage you/your users can correct possible
errors forwarding as attachment the good email found in
/spambox imap folder (or spambox pop3) to
assp-notspam@clientdomain.com and forwarding as
attachment spam found in inbox to
assp-spam@clientdomain.com .
As admin , you can do these corrections also using ASSP WHM > SPAM ANALYZER
and NOT SPAM ANALYZER
and the ASSP WHM > SPAM FINDER.
Using these ways you can speedup
the process to build an efficient spam database (Bayesian and HMM databases). Your users can receive a
list of blocked spam (anytime they want) by sending an email to
asspblock@clientdomain.com (the email includes commands to resend the
blocked email too).
How to set your ASSP
more aggressive
ASSP v1
If you are using ASSP
v1 after 2/3 weeks of usage (or before depending on your email traffic,
more traffic is better) you may go to ASSP WHM > SCORE SETTINGS > and
increase Bayesian to 44-45 (SET SCORES to save). After 1/2 months of
usage if rare spam is passing go to ASSP WHM > SCORE SETTINGS > and
set/increase Bayesian to 46-48 (SET SCORES to save) .
ASSP v2
If you are using ASSP v2 after 2/3 weeks of usage (or before depending on your email traffic,
more traffic is better) you may go to ASSP WHM > SCORE SETTINGS > and
set Bayesian to 12 , HMM to 43 and
PenaltyMessageLimit to 50-53 .
If you have a local to local email blocked remember that
ASSP never blocks a local sender .
If it happens it means that the local sender is sending email incorrectly
(as a relayer , spoofer i.e.) .
To fix the "issue" simply be sure your customer is sending email
correctly
SMTP mail.customerdomain.com (or server hostname)
using one the available ASSP ports ( by default 25, 26 ,587 or 465 SSL ) .
Automatic whitelist
ASSP creates an automatic whitelist based on the
customer usage. Each time a local customer send an email the sender is
automatically whitelisted. Also for this reason using ASSP your customer should not be
worried with whitelist. The automatic whitelist will work only if the
customer send email correctly using
SMTP mail.customerdomain.com (or server hostname)
If you have a good remote sender email blocked you should note to your customer that all
blocked
email are collected and can be retrieved in several ways here explained
http://www.grscripts.com/howtofaq.html#88j
By default all blocked email will bounce to the sender with an autogenerated NOSPAMTAG
code. If the
sender receives the bounce he can also resend the email including in the email the
NOSPAMTAG code .
This is an example of bounced error message received by the sender when an email is blocked
by your ASSP.
554 5.7.1 Mail appears to be unsolicited, resend
with the code U7827H23 appended to subject and ask to have your email
whitelisted (the code U7827H23 changes each 24 hours).
3)
Delaying (also
known as greylisting) filter permits to block a good amount of SPAM at
early stage ( more info
here
),
however please consider following points ;
reasons not to
use
- its behavior could create some confusion to unexperienced users
- SPAM SCORING is more efficient than delaying
filter, some spam could pass
- the email rejected due to delaying filter cannot be retrieved using the SPAMBOX@
plugin.
There is no spam collection using delaying
filter
- your Bayesian (and HMM) database can't be populated
using delaying.
reason to use
-
very useful to reduce email traffic , for example if your server is under a
huge spam attack
I recommend to start your ASSP
with delaying OFF for all your users . You
can do that by opening your ASSP WHM INTERFACE , click "ASSP DOMAIN CONFIG"
and turn
OFF for ALL your domain/users, the Delaying filter .
Your users can decide anytime to turn delaying
filter ON(/OFF) using their cPanel frontend .
NOTE : Set also delaying
OFF by default for all new hosting accounts using
the "DEFAULT SETTINGS" > FILTER
STATUS DEFAULT SETTINGS in your ASSP WHM interface , so
that new hosting users will receive delaying off/disabled automatically
; note that this setting will be applied only to new hosting accounts and it will
NOT apply/work to transferred accounts . If you will
transfer accounts from other server by default they will have the delaying
filter enabled (does not matter the
the "DEFAULT SETTINGS" values)
. You can turn it OFF using ASSP WHM > "ASSP DOMAIN CONFIG" > delaying
filter , set the filter delaying OFF for each transferred account.
4)
You and your users should read all the "HELP" section included
in their ASSP Deluxe for cPanel frontend ( "HELP" button
near the Change Language drop down ).

Be sure they read how to use
the ASSP email interface to report false positives or spam (
assp-spam@ assp-notspam@ .....) and also
this
article . Also be sure you read
below how works the "no local address"
spam filter.
After the installation the "no
local filter" is enabled by default
for all users/domains . It's one of the most
important filters .It permits to block
email dictionary attacks and at
the same time it permits to collect a
"bad ip" list.
When the "no local filter" is
enabled you allow ASSP to receive email
only to existent email addresses on
your server (pop3 and
forwarders) stopping every kind of
email dictionary attack (each
email sent to random_word@domain.com
will be stopped) . The sender
which sends an email to a not existent
email on your account (i.e.
random_word@clientdomain.com ) will
receive following error : 550
5.1.1 User unknown:
random_word@clientdomain.com . When
this filter is enabled the client lose
"default address"
functionality .
So if you have several accounts using the
"default address" you have 2 options .
1) You may advice your users
that with the "no local filter" they can
receive email only to existent pop3
accounts and forwarders so the
user can decide if it's the case to
disable the filter using the ASSP Deluxe
for cPanel frontend.
2) You may turn off for all or some
clients the "no local filter"
using the WHM ASSP web interface (ASSP
DOMAIN CONFIG) . If you want set off
"No Local" also for new hosting accounts
automatically , go to ASSP WHM > ASSP
Deluxe for cPanel tools > DEFAULT
Settings > FILTER STATUS DEFAULT
SETTINGS > and set "No Local" to OFF .
|
|
|
Example of a message blocked due to invalid address
(no local filter) [InvalidAddress]
Feb-29-12 02:47:48 id-33050-00954
[InvalidAddress] 22.7.27.4 <ino@or.com> invalid address rejected:
wheeler@local.net;
5)
(#005) ASSP
NEVER block or "filter" a LOCAL email ; a
local sender should be fully allowed by ASSP , always. If it's
not happening, be sure your customer is sending email correctly using
SMTP mail.customerdomain.com (or server hostname)
and
using one the available ASSP ports ( by default 25, 26 ,587 or 465 SSL ) .
ONLY
using this way ASSP will never block a local email and will able to build an
efficient Bayesian (and HMM if you use ASSP v2) filter and an automatic whitelist database. By default your
users can send email using the port 25
or the alternative port 26 or 587 (by default ASSP installation) . The
alternative ports can be configured using the ASSP Web interface and
MUST NOT configured/enabled in your WHM > Services section .
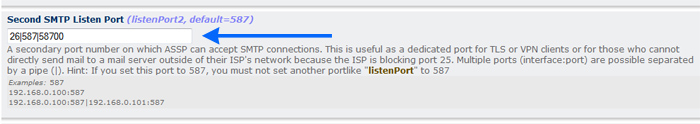
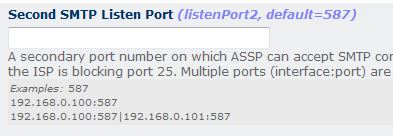
If you want add other SMTP ports open the ASSP Web Interface > Network Setup
menu >
Second SMTP Listen Port (listenPort2) and enter alternative
ports separated by a pipe. For example if you want have alternative
ports 26,587 and 58700 you should enter 26|587|58700 in
listenPort2. Do not enter here SSL port 465
(you can enable ASSP SSL using ASSP WHM interface > SSL MENU) !
Apply/Save
ASSP settings and be sure to allow the TCP ports in your local or/and
external firewall .
Example of usage
If the isp blocks port 25 and 26 and the customer can't
send email , simply set an uncommon alternative port
for example 56384 .
Open the ASSP Web Interface (http://your_server_ip:55555) > Network Setup >
Second SMTP Listen Port (listenPort2) and enter 26|56384
or only 56384 (if you want have 25 and 56384), save ASSP
settings.
Be sure to allow the port 56384 TCP IN/OUT Open the port in your
firewall. Now report your user which is not able to use port 25 to send
email using SMTP port 56384 . The isp will not block this uncommon port
and your user will be able to send email correctly using
SMTP
mail.clientdomain.com (or your hostname).
6) .
(#.6) Enable the SPAMBOX@ plugin using WHM ASSP,
so your users can
easly track false positives , no blocked email will be lost , and
the user can report (
forwarding as attachment ) false positives as good
email
by forwarding the email to
assp-notspam@clientdomain.com : if you have read point 4) above you
should already know how works the
ASSP Email Interface
(assp-spam , assp-notspam and other commands).
NOTE that you can use a NOT REGISTERED domain name to setup your
spambox plugin. The main spambox domain MUST NOT
be a reseller
account and it can't be your hostname . The main spambox domain
must have CGI functionalities . When you enable the spambox plugin you will see other features on
your ASSP WHM ; you will be able to enable/disable imap spambox per domain ,
and you will be able to enable/disable "SPAM DAILY REPORTS". Also your
users
will have a new button/functionality on their cPanel frontend (SPAMBOX
near the "change language" dropdown)
where they can receive help and disable/enable each spambox feature.
You can read all possible ways to read a blocked email here
http://www.grscripts.com/howtofaq.html#88j
 |
cPanel
and ASSP spambox :
#sp01 .#900
-
spambox
collection is possibile only is you
use
maildir
mail
storage ( default cPanel mail
storage ) .
spambox
collection using mdbox
mail storage
is not
possible.
-
Dovecot mail
compression (WHM > Service
Configuration > Mailserver
configuration) must set OFF
( default
cPanel )
otherwise spambox collection will
not work .
|
|
|
 |
3
minutes ASSP Deluxe for cPanel spambox
setup |
|
! |
If you are receiving the message "Your
spambox is not working" in
your ASSP WHM first of all check if your
cPanel internal php is working correctly
, go to console and execute this |
|
# /usr/local/cpanel/3rdparty/bin/php-cgi -v
If the command above returns errors
please open a ticket with cPanel and ask
to have cPanel internal php fixed (in
most situations a cPanel update could
fix this issue automatically). It will
fix the issue with your spambox too. If
the command above does not return errors
please try reinstalling your spambox
following the instructions below. |
|
|
- Open your cPanel WHM , go to "Create a
new Account" and create a fake account
spamxyz.us owned by root
with cgi capabilities
- now execute
# nano /etc/valiases/spamxyz.us
and add this line ,
be sure to
include also the #
#
spammaster@spamxyz.us:
"|/usr/local/assp/deluxe/piping_b.php"
.. save
the file
(CTRL + O) and exit
(CTRL + X)
now execute this ( to create a
pop3 collector for your spambox )
and replace
random_password
with a random password of your
choice.
# /scripts/addpop
spammaster@spamxyz.us -password
random_password
- now open your ASSP WHM interface >
click SPAMBOX and
enter the email
spammaster@spamxyz.us
now execute
# crontab -e
and enter following cronjobs (
between rows
MAILTO="" and MAILTO="root" )
*/4 * * * *
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/spam_cronjob.php
10 8 * * *
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/clear_spambox.php
sday=8 sp=yes limitspace=10000
remdays=4
the clear_spambox.php cron removes
automatically from accounts spam
(from imap /spambox folders) older than 8 days
(sday=) and
remove additional 4 days ( remdays=
) of spam if
the /spambox folder is greater than
10 MB (limitspace=10000) . You can customize
as you would limitspace, remdays and
sday . -
now using ASSP WHM , you can
enable "spambox" and "daily spam
reports" per user . Your
users can do the same using
the ASSP Deluxe for cPanel frontend.
-
You can test if spambox is working
in this way
# tail -f
/var/log/exim_mainlog | grep -A1 "spammaster@spamxyz.us"
SPAMBOX
Frequently Asked Questions:
.
1. Where
do I go to change the wording for
the SPAMBOX DAILY SPAM Report ?
/usr/local/assp/deluxe/emailreport.php
2.
How do I
change the from address for SPAMBOX
DAILY SPAM Reports ?
Add to the cronjob:
clear_spambox.php cemail=youremail@yourdomain.com
Example :
10 4 * * *
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/clear_spambox.php
cemail=name@yourdomain.com
3.
How do client's check their SPAMBOX?
Primary
way :
By using any imap powered email client
or any cPanel Webmail
(Horde,Squirrel,Roundcube) and checking
the /spambox imap folder.
Secondary way :
Log in
to your cPanel, then click on the SPAM
and Virus Protection ASSP icon. To view
the SPAMBOX Help and
configuration guide, click the red
SPAMBOX button near the top of the page.
More
detailed information here
http://www.grscripts.com/howtofaq.html#88j
As admin :
ASSP WHM > SPAM FINDER
4. I have a cPanel
license with only ONE account , can I
install spambox ?
and setup the spambox , but you
should install spambox over your
customer domain , instead to use
spamxyz.us .
|
|
|
|
|
7) Using the
GUI .
If you
want reduce issues you should avoid to change settings in ASSP web
interface if you are not sure what are you doing . You can use ASSP Web interface to whitelist a
domain, set to noprocessing domain or email , spamtrap an email , change scoring
settings and so on
.
Customization of following ASSP menus is
strongly not recommended , you may break ASSP Deluxe compatibility
- Network setup
- Test mode
- Spam Control
- Spam Lovers/Haters
- File Paths
- Copy Spam/Ham
- LDAP setup
- SSL/TLS
- Collecting
- Automatic update / Restarts
- Logging
- Administration interface , use it only if you need to change the
webAdminPassword
Customization of
following ASSP menus are for expert/advanced users
- Configuration Sharing
- Network Setup
- SMTP Session limits
- DNS setup
- Email Interface
- Block Reporting
- Scoring Settings
- Validate HELO
- POP3 collecting
Usage/knowledge
of following ASSP menus is recommended for daily antispam maintenance
- Whitelist
- No Processing
- Control Outgoing
- Regex/Bombs
 |
There are some ASSP parameters which
are controlled/modified automatically by
ASSP Deluxe. If you want customize them
using the ASSP Web Interface you should
first set them to OFF
in your ASSP WHM > AUTOMATION
SETTINGS page so that your
custom values will be preserved in your
ASSP WEB interface. |
|
|
8)
#stop How to
disable temporarly ASSP . There is no need to
uninstall ASSP if you are experiencing a temporarly problem
and
you want return temporarly to the mailserver cPanel way (ASSP fully disabled).
So if you want FULLY disableASSP and return to cPanel/EXIM
usage you should follow these simple steps ;
You should click ASSP
STOP in your ASSP WHM
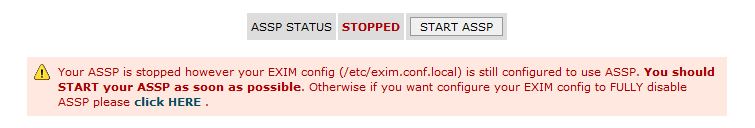
You will receive the message above. If you click the
"click HERE" link , ASSP will be fully
disabled
and EXIM will be unproxied from ASSP , normal cPanel usage
with ASSP disabled.
You will receive this message
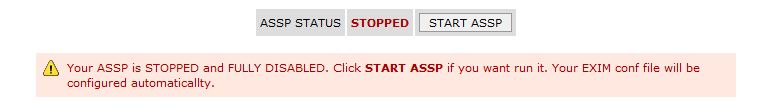
Edit your root cron list ( crontab -e ) and
comment/disable (#) the status.php cron in this
way, to avoid any automatic restart of your
ASSP.
# */4 * * * *
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/status.php
EXIM is now working without ASSP , normal cPanel/EXIM
only usage.
To re-enable
your ASSP
Edit your root cron list ( crontab -e ) and
remove the comment/disable (#) from your
status.php cron , you should have this
*/4 * * * *
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/status.php
Now go to ASSP WHM and click START ASSP ; EXIM will be reconfigured correctly and ASSP
should restart after 20-60 seconds depending on your ASSP version (v1 or v2) .
 |
What does happen when I click
START ASSP ? |
When you click "START ASSP" ,
your
/etc/exim.conf.local file
will be configured with following lines
@CONFIG@
local_interfaces = 127.0.0.1
daemon_smtp_ports = 125
which allows ASSP to proxy email to
EXIM. After this step EXIM and ASSP are
started so that ASSP can start to
process email. |
|
|
 |
What does happen when I click
STOP ASSP ? |
|
If your ASSP is running
and you click "STOP ASSP" , ASSP is
temporarly stopped however note that the
daemon_smtp_ports in EXIM
is still active.It will be underlined by
the warning below. At this point you can
START ASSP or..
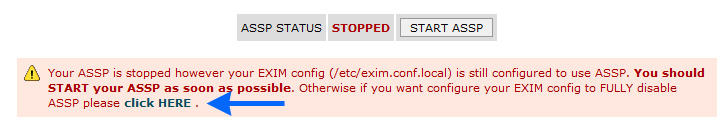
... only if you want fully disable ASSP
and return to normal cPanel usage (only
EXIM) you should click the "click
HERE" button in the image
above. ASSP Deluxe will remove following
lines from your /etc/exim.conf.local
file
@CONFIG@
local_interfaces = 127.0.0.1
daemon_smtp_ports = 125
and will fully disconnect
ASSP from EXIM, returning to
normal cPanel usage (only EXIM)
. |
|
|
9) .ASSP uses DNS very often to executes
DNS antispam checks. If your DNS is slow you should fix
your
/etc/resolv.conf . You can test your DNS speed using following
ASSP Deluxe for cPanel command
# cd /usr/local/assp/deluxe;/usr/local/cpanel/3rdparty/bin/php-cgi
dns_check.php
The test will be completed in about 1 minute .
How to
configure ASSP for max DNS performance ( #DNS_fast
)
You can configure DNS for your ASSP using following way ;
install namebench in this way
# cd /usr/local/assp/deluxe;git clone
https://github.com/catap/namebench.git;cd namebench
Excute namebench
# cd /usr/local/assp/deluxe/namebench;./namebench.py -s all
--template=resolv.conf
take a break, it will need about 10 minutes to
execute. At the end you will receive something
like this
- Saving report
to /tmp/resolv.conf
- Saving detailed results
to /tmp/namebench_2018-10-10_1053.csv
The file
/tmp/resolv.conf will contain
best/fast 3 nameservers to be
used in your /etc/resolv.conf and/or in your
ASSP !.
for example
nameserver 156.154.71.1 # UltraDNS (2)
nameserver 62.210.16.6 #
SYS1-62.210.16.6
nameserver 74.82.42.42 # Hurricane Electric
If you want use them in your ASSP (
recommended!
) first execute this
# echo "DNSServers" >>
/usr/local/assp/deluxe/no_auto_settings
now open your ASSP WHM interface
and open your ASSP WEB INTERFACE
. Open the DNS Client SETUP
menu and enter in DNS Name
Servers* (DNSServers) the nameservers
above separated by a pipe (|)
156.154.71.1|62.210.16.6|74.82.42.42
Save/Apply ASSP settings , your ASSP is now
configured with best DNS settings .
note : If your DNS is slow also remove
any "search .." row in your /etc/resolv.conf if you have anyone,
and restart your DNS.
10)
Enable ASSP SSL using the ASSP WHM INTERFACE >
SSL MENU .
#ssl_config
Open your ASSP WHM interface > SSL MENU and
enable ASSP SSL .
You can enable STARTTLS for all your
SMTP ports, listenport (25) and listenport2 (26,587,
and other if you have set them in
ASSP) plus 465 SSL. You can enable or disable
STARTSSL for all your server listenport(s) .
NOTE : TLS
settings in WHM »Service Configuration
»Mailserver Configuration
rules over ASSP SSL
settings . So If you set
strict TLSv1.2 in Mailserver Configuration (
SSL Minimum Protocol ) only TLSv1.2 email
will be accepted ,
does not matter ASSP SSL_version settings.
NOTE :
ASSP handles SSL connections by using
IO::Socket::SSL Perl module .
Default cipher list and SSL version used by IO::Socket::SSL (and
ASSP) are the following .
(
this applies to
IO::Socket::SSL version 2.066 ,
if you are using an older or newer
IO::Socket::SSL decompress the IO-Socket-SSL
package and check the SSL_cipher_list an
SSL_version contained in SSL.pm file )
These are
secure values which are compatible with the rest
of the world and exclude broken ciphers that are clearly broken
and dangerous.
SSL_version = SSLv23:!SSLv3:!SSLv2 # consider both SSL3.0 and
SSL2.0 as broken
SSL_cipher_list =
ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:ECDHE-RSA-DES-CBC3-SHA:ECDHE-ECDSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:DES-CBC3-SHA:HIGH:SEED:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!RSAPSK:!aDH:!aECDH:!EDH-DSS-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA:!SRP
If you want a wide compatibility,
compatibility to most legacy email clients be
sure you have
SSL Minimum Protocol set to TLSv1
(SSLv3 not recommended!) in WHM
»Service Configuration »Mailserver Configuration
.
On the countrary if you want a
strong security ( and PCI compliance ) and
allow only newer email client (updated to latest
TLS protocol) be sure you have
SSL Minimum Protocol set to
TLSv1.2 in WHM »Service Configuration
»Mailserver Configuration .
- more
info about TLS protocols and cypher strings
here .
- how to check your server
allowed protocols and cypher strings
here .
11) Be sure
your ASSP Deluxe is always configured as recommended in the ASSP Deluxe
for cPanel checklist
http://www.grscripts.com/advice2.html (this link is always available in
your ASSP WHM interface)
12) Read
all the FAQs in this page as possible . Recommended articles
ASSP advanced settings
using
find_abusers.php
Unofficial clamD signatures to block spam/virus/malware
(by HOW TO you already have them installed)
With ASSP and ASSP Deluxe you can reduce risk of
outgoing SPAM #out
by applying these (all enabled by default except of
ASSP scoring for local senders) ;
13) If you have ASSP
installed on more than 1 server , you should whitelist all the ips
of your ASSP servers
Open the ASSP web interface >
Whitelisting/Redlisting menu > Whitelisted IPs and whitelist the ips
of your other ASSP servers . DO NOT enter local ips in Whitelisted IPs
.
14).
If you your user will experience big delays
to send email or smtp timeouts sending email
Exactly
when you are experiencing delay to send email (or smtp timeouts to send
email) , open your ASSP WHM and click the SMTP CONN button . If you
see a lot of* simultaneos smtp connections your server is under an
email attack which your server is not able to support , this could
be due to (#14) ;
a) server DNS slow
b) server under heavy email attack
(number of ASSP smtp sessions is too high to be supported) .
c) server internet connectivity very
slow
d) kernel outdated
e) os outdated
If you can't fix the points above you can solve using one of the following
ways :
1) Upgrade to ASSP 2.x here
. ASSP 2.x works multithreaded and is able to manage much more SMTP
connections than ASSP 1.x .
2) If solution 1) is not possible , set delaying ON for all your domain
names using ASSP WHM > ASSP DOMAIN CONFIG
3) If solution 1) or 2) is not possible, you may bypass ASSP for one or more
listen ports . You may configure ASSP for incoming
spam using port 25 , and EXIM (bypassing fully ASSP) for
outgoing smtp . Using this way smtp outgoing will be very fast also if
you have a lot of smtp sessions in your ASSP .
Suppose you have set port 25 in listenPort and 26 and 587
in your ASSP listenPort2 as follows (assp web interface > Network
menu)

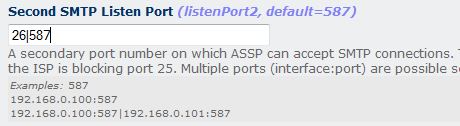
Now if you want use 25 for incoming, to filter ALL incoming SPAM
using ASSP and port 26 and 587 for outgoing smtp
bypassing ASSP, first empty listenPort2 and Apply Changes in your ASSP as
follows
now open your EXIM configuration manager and click Advanced Editor
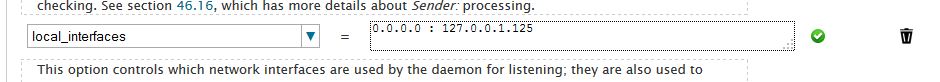
Now apply the following changes to local_interfaces .., replace 127.0.0.1
with 0.0.0.0 : 127.0.0.1.125
and daemon_smtp_ports .., replace 125 with
26 : 587
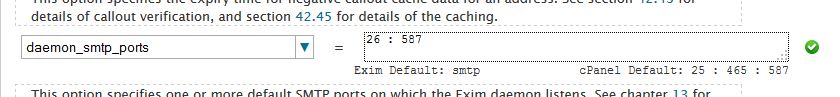
Now SAVE EXIM settings .
Now edit Squirrel webmail to send email using port 587 ,
# nano /usr/local/cpanel/base/3rdparty/squirrelmail/config/config.php
and change $smtpPort = 25; with $smtpPort = 587
Save the file
Now edit Roundcube webmail to send email using port 587 ,
# nano /usr/local/cpanel/base/3rdparty/roundcube/config/config.inc.php
and change $rcmail_config['smtp_port'] = 25; with $rcmail_config['smtp_port']
= 587;
Save the file
After these changes ALL incoming SPAM will be filtered by ASSP ; port
26 and 587 will be available for outgoing smtp
directly to EXIM and bypassing fully ASSP .
|
Good points : |
Your customers can send email with
no delay directly to EXIM.
Useful if you need a fast smtp port to
send large attachment or mailing list
without overloading your ASSP with
outgoing legitimated activity.
|
|
Bad points |
ASSP email interface commands (
assp-white@ , asspblock@, assp-spam, and
so on ) will be available only using
smtp port 25 .
No automatic whitelisting using ports 26
and 587 , only using port 25
If you want secure ports 26 and 587 in
the example configuration above your
should turn OFF ASSP SSL for all your
smtp ports using your ASSP WHM > SSL
MENU.
No control for outgoing email executed
by ASSP when using ports 26 and 587
(i.e. email size, outgoing spam
protection if enabled) |
|
|
NOTE: if you would have also SSL 465 with
EXIM (bypassing fully ASSP) you should do this
- fully disable SSL in your ASSP using ASSP WHM > SSL MENU
- in exim configuration advanced add port 465 , so you will
have
26 : 587 : 465
Save exim , and ignore the exim restart failure.
- Now execute this
# touch /usr/local/assp/deluxe/465off
# /usr/local/cpanel/3rdparty/bin/php-cgi /usr/local/assp/deluxe/status.php
- Restart ASSP and EXIM
Now you should have
- port 25 for incoming/outgoing in your ASSP
- port 26,587,465SSL for smtp outgoing fully bypassing ASSP
15)
(#15A) Subscribe to
ASSP Deluxe for
cPanel Mailing List to be notified
in case of important updates (you
can subscribe below)
|
ASSP Deluxe
for cPanel mailing list. |
16) Before
upgrading always read carefully the
changelog
If you would rate ASSP
Deluxe for cPanel please
click here , thank
you , your support is important.
Which is the required cronjob to use ASSP ? ( #04 )
only this
10 4 * * * cd
/usr/local/assp;perl /usr/local/assp/rebuildspamdb.pl
Which are required cronjobs to use ASSP Deluxe for cPanel ? ( #0002 )
If you followed the how to , you have already set cronjobs
as required , here you can
read again more info about required cronjobs .
following 2 cronjobs are required to mantain your list of local
email updated
*/59 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php
*/3 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/update_email.php
following cronjob is required to mantain a list of bad ips (please be sure
to enter it on a single line)
*/20 * * * *
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/find_abusers.php
sw=39 rl=50 dc=40 on=1
following cronjob is required to restart ASSP automatically ASSP if it
crashes
*/1 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/status.php
following cronjob is required for a better spam detection using clamd (more
info)
30 7 * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/signatures.php
If you don't want receive email notification each time these cron
executes enter them at the end of your cronjob list in this
way (please avoid the "> /dev/null" solution , since it
DOES NOT
work with these scripts.)
MAILTO=""
*/59 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php
*/3 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/update_email.php
*/3 * * * *
/usr/local/cpanel/3rdparty/bin/php-cgi /usr/local/assp/deluxe/status.php
*/20 * * * *
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/find_abusers.php
sw=39 rl=50 dc=40 on=1
30 7 * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/signatures.php
MAILTO=root
 |
If you do not use MAILTO
between your ASSP deluxe cron jobs, your
mail queue could increase
considerably,
making your mailserver
very busy.
For this reason I strongly recommend the
usage of MAILTO between your ASSP Deluxe
cronjobs. |
|
|
If you install the SPAMBOX@ plugin you should use also
*/5 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/spam_cronjob.php
26 3 * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/clear_spambox.php
Also for these 2 cronjobs if you do not want receive email notifications put
them between MAILTO="" and
MAILTO=root.
what are spam_cronjob.php and clear_spambox.php ?
spam_cronjob.php is required to use spambox@ .
clear_spambox.php run each day , removing @spambox email on all your
user accounts older than 7 days (by default 7 days) . If you want
change the default (7 days) you should enter the cron in this way
10 4 * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/clear_spambox.php sday=n
and replace n with your days. For
example ...
10 4 * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/clear_spambox.php sday=15
removes spambox@ emails on all your user accounts older than 15 days.
Which are required cronjob to update clamav
antivirus signatures ?
following cronjob mantains your clamd signature file
updated . You can execute it daily.
10 12 * * * /usr/bin/freshclam --quiet
--daemon-notify
I am receiving licensing errors , what to do now ?
Go to console and try executing this
# cd /usr/local/assp/deluxe
# wget -r -nH --cut-dirs=10
http://www.grscripts.com/assp150/deluxe/license.deluxe
# mv -f license.deluxe license.php;chmod 755 license.php
Do we just need one license for the overall server, and the accounts hosted
on the server will be covered, or would we need a license for each site that
is using a static IP?
You need to license 1 ip per server (such as with cPanel license). You do
NOT need a license for each site that is using a static IP .
You should license only the ip returned by this command in your
server
# lynx -dump
http://www.cpanel.net/showip.cgi
does ASSP interfere at all with the cPanel catch-all emails? Those don't
seem to be working any more...
Yes if a customer is using "NO LOCAL" filter enabled
http://www.grscripts.com/howtofaq.html#52
If you would block all email dictionary attacks you cannot at the same time
using "catch all" and the "no local filter" enabled .
Your customers should decide between "no local" ON and "catch all" usage .
If a customer would use "catch all" he should disable
"NO local" filter for his domain(s) using the ASSP Deluxe cPanel frontend.
1- Using "catch all" you open infinite doors to spammers
2- Using no local ON you allow only few ports (valid email) to spammers and
you can collect ips of invalid attacks (using penalty box, fid_abusers.php).
If you want make spammer life harder you should not use "catch all".
Is it possible for ASSP to block or drop an email when a particular word is
used in the subject line of en email or body. do ASSP support clamAV
YARA rules ? #yara
There are countless ways to block or score email based on email content
using ASSP, for example you can use all the options in
Perl
Regular Expression Filter and Spambomb Detection in ASSP Web Interface
, you can score or block emaik if a particular word or regex is used in
subject, and/or email header, and/or email body.
I'm happy to announce client defined custom YARA rules are now
available for ASSP Deluxe for cPanel ( ASSP Deluxe 10.x and above)
. YARA is a tool used
mainly, but not exclusively, for identifying and classifying malware
based on string or binary pattern matching.
You can use YARA rules to manage and enhance detections, stop the
latest threats. You can now introduce your own YARA rules to enhance
your detection efficacy.
You can add
clamAV YARA rules in the file
/usr/local/cpanel/3rdparty/share/clamav/
custom_spam.yaraif you want
block SPAM using YARA rules
How to use YARA here
http://virustotal.github.io/yara/ Writing YARA rules
https://yara.readthedocs.io/en/v3.11.0/writingrules.html
https://seanthegeek.net/257/install-yara-write-yara-rules/amp/
A rule is a description based on textual or binary patterns. A rule’s
description can be broken down into three sections:
Together, these sections determine a rule’s logic. At a minimum,
every rule must have a condition section. You may omit the meta or
strings section if not needed.
After entering a YARA rule be
sure to restart ClamAV ( # /usr/local/cpanel/scripts/restartsrv_clamd )
, if it restarts correctly the YARA rule was accepted and correct.
ASSP Deluxe includes an updated (updated daily using
signatures.php cronjob) YARA rule file located here
/usr/local/cpanel/3rdparty/share/clamav/
grscripts_spam.yara .
It includes new SPAM patters and it's continuosly updated
with new rules
.
YARA rules can be used
to detect and block various types of threats, and now with the
capability available in ASSP Deluxe for cPanel, organizations can apply
their own custom rules against attachments, email headers, and the body
of emails to help detect threats. With this feature, you can gain
more control to manage email flow and detect threats in custom and
creative ways.
Can ASSP drop the mail and not send it to spambox ?.
If you want drop an email without passing it to spambox , you should use
Do Not Collect Messages - Content Based* (noCollectRe) in the Collecting SPAM and HAM
ASSP web interface menu.
You may also use "Do
Not Copy Messages Above This MessageTotal score (ccMaxScore)"
and Messages whose score exceeds this ccMaxScore
threshold will not be copied in spambox. For example: 90
My customer has a good email blocked (false
positive) , what to do now ? .
Does ASSP offer a front-end interface for users to manage their blocked
email ?
[#88j]
In ASSP there are
Bayesian collections (spam/not spam/ok mail..) which can be corrected using
a web interface (by administrators) or email interface (by customers) to
make the Bayesian filter more efficient. All the blocked spam is also
collected in customer spambox .
If a customer need instruction to read/find a blocked email he can read
the documentation by clicking the HELP button included on ASSP deluxe cPanel frontend (HELP button
near the Change Language drop down).

Below you can read all the ways available to read a blocked email , customer and
administrator.
If a customer info@domain.com (i.e.) has a good email blocked , he
can
1) The customer can read the /spambox imap folder (faster way)
or read email using Horde , Squirrel and Roundcube (info@domain.com spambox
folder). When the customer will find/search the blocked email he can
forward as attachment it to
assp-notspam@domain.com , and it will
not be blocked again.
2) The customer can send an email to asspblock@domain.com (from
info@domain.com).
Your customer will receive via email a list of blocked email . If the client
find a good email blocked in this list
he can press the button to receive/release the email in his inbox.
3) the customer can send an email to the sender and the sender will be
whitelisted automatically
4) the customer can whitelist the sender email
also by sending an email to assp-white@domain.com and adding the email in
the email subject (ASSPv1) or email body (ASSPv2) .
6) the customer can setup a spambox@domain.com pop3 spambox
collector. For all customers which are not confident with imap protocol they
can use a spambox collector . All spam sent to @domain.com will be collected
by a spambox@domain.com pop3 account. When the customer will find a good
email blocked he can forward as attachment
the email to assp-notspam@domain.com , and it will not
be blocked again.
All the steps above can be done without administration support. Your
customer can find all the instructions above and more
by clicking the HELP button in their ASSP Deluxe cPanel frontend.
As Administrator you can support your customer also using the new SPAMBOX
FINDER in your ASSP WHM interface you can you check spam
collected in your customer spamboxes. You can release email or whitelist
sender too.
As Administrator you have other ways to allow a blocked email using
the ASSP web interface or your ASSP WHM.
For example you can put the blocked email in ASSP WEB INTERFACE >
whitelisting menu > Whitelisted Domains and Addresses* (whiteListedDomains)
, you can whitelist ip senders , you can use the noprocessing menu to bypass
domain,email ,ips ..
If several customers are reporting good email blocked, you (as
administrator) should set ASSP spam filter settings
more conservative , it can be done almost instantly using ASSP WHM > SCORE
SETTINGS and decrease bayesian contribute to 40-43
Good email email blocked in spambox should be rare or none , otherwise it's
time to reconfigure your ASSP settings.
If you are using ASSP 1.9.x or above your customer can set custom spam settings
per domain too .

 |
NOTES
A) If after whitelisting an email
or domain , you still not receive the
email from remote sender , it means the
remote sender ip address has been
collected in the IP Blocking (ASSP Web
interface > IP Blocking >
denySMTPConnectionsFrom or
denySMTPConnectionsFromAlways ip
collections) . In this case if you know
the sender ip address (you can grep the
ASSP log to find the sender ip address)
you can allow the ip using ASSP WEB
interface > Whitelisting menu >
whiteListedIPs ; if you don't know
the sender ip address simply go in your
ASSP WHM and click FLUSH IP BLOCKING.
B) You should never
whitelist a local domain or local email
using your ASSP Web Interface. ASSP
already fully allow local
domain and email . If ASSP is blocking a local sender please
read this.
C) The ASSP whitelist file is
stored on /usr/local/assp/whitelist. You
should not edit this file since it's
generated automatically. |
|
|
I just got done removing a bunch of ip addresses from
denySMTPConnectionsFrom and denySMTPConnectionsFromAlways. Can you tell me
how these addresses get in these files and if there is a way to allow these
?
The ips are populated by
find_abusers.php
cron. If you have an ip which you want allow forever and it's in
denySMTPConnectionsFrom and/or denySMTPConnectionsFromAlways do the
following
1) put the email or domain which should pass in ASSP WEB INTERFACE >
whitelisting menu > Whitelisted Domains and Addresses* (whiteListedDomains)
2) then open your ASSP WHM and click "FLUSH IP BLOCKING"
Do you support secondary home locations ?
[#89]
yes , the secondary home location (i.e. home2)
is automatically detected. Only please be sure to set
*exactly * the
secondary alternative home location on WHM > "Basic cPanel/WHM Setup"
> "Home Directory Prefix". For example if your seconday
home location is /home2 you should enter home2 .
With ASSP Deluxe 4.0.0 and above versions also 3rd and
4rd home locations are supported . So , if you have more than 2 home
locations please follow this guideline ; go to console/SSH and execute this
# nano /usr/local/assp/deluxe/home
and enter a list of your home locations one by line , for example
or if you have 4 home locations ...
save file (ctrl x) and exit . (
<= ! return ! <= )
Now if you would test the home locations, go to console and execute this
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php show=1
Then check if your /usr/loca/assp/deluxe/assp_local_email e
/usr/loca/assp/deluxe/assp_local_domains contains all email and domain from
your home locations .
How to monitor assp status ( #19 )
If you followed the how to , you should are already monitoring assp status
using status.php cronjob.
You can read more info
here.
How to change/customize language or html for your ASSP deluxe for cPanel frontend
?
By default the ASSP Deluxe cPanel frontend will use the english language . If you
want use another language style or if you want change something on
the html layout please
read here .
How
can I turn off ASSP filtering for some accounts ? ( #71 )
If you followed the post installation step you should have
already ASSP scoring ON on your ASSP Deluxe WHM interface.
By default your clients have following filters (on ASSP Deluxe cPanel
frontend)
assp scoring
delaying
no local
antivirus
by default your clients can't turn off ASSP scoring , however
you can allow them to turn ASSP scoring OFF or ON using
ASSP WHM> ASSP SCORING MODE > ENABLE ASSP SCORING MODE USER CONTROL
Once you have done this step, the client can turn off/on also "ASSP Scoring"
using the ASSP Deluxe cPanel frontend , and you can do that too using
ASSP WHM> ASSP DOMAIN CONFIG > Score
How to disable ASSP fully for a domain or email
If you are using ASSP v1
If you would FULLY disable ASSP for a client domain (antivirus included) you
should add @customerdomain.com
or user@customerdomain.com (if you would
exclude an email)
in
ASSP web interface > Validate sender > NoProcessing Sender*
(noProcessingFrom)
ASSP web interface > Validate recipient >
NoProcessing Recipients* (noProcessingTo)
If you are using ASSP v2
If you would FULLY disable ASSP for a client domain (antivirus included) you
should add @customerdomain.com
or user@customerdomain.com (if you would
exclude an email)
in
ASSP web interface >
No
Processing - IP's, Domains, Addresses and Limits > No Processing
Addresses (noProcessing)
note : If you add TO addresses here, all
recipients for a single mail must be marked as noprocessing to flag the mail
as "noprocessing".
If you want be sure a
client/local domain or email will go in noprocessing in each case
I recommend you to use
Regular Expression
to Identify No Processing Mail* (npRe)
and add
the domain or email using Regex . i.e.
email\@domain\.com
\@domain\.com
Other ASSP v2
noprocessing methods are available in the "No
Processing - IP's, Domains, Addresses and Limits"
menu (i.e.
noProcessingIPs,noProcessingFrom,noProcessingDomains)
. Please read the help description included in
your ASSP GUI.
What should I do when I transfer an hosting account on a server
running ASSP Deluxe for cPanel (45)
each time you transfer an account from another server you should execute
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php
in this way the email/domain for the transferrred account will be
immediately available for ASSP usage.
Otherwise they will be available in max 59 minutes ( ex_localdomains.php
cron execution )
Also be sure to disable delaying
for the transferred account using the "ASSP DOMAIN CONFIG"
in your
WHM ASSP
Deluxe interface
How to
move "assp deluxe for cpanel" from an old server to new server
(#34)
You should follow these steps to move "ASSP Deluxe for
cPanel " from an old server to a new server.
 |
If you would, I can move/install
ASSP Deluxe for cPanel on a new server
for you ; order a
migration service
then email me with
your old ip and new server ip and your Paypal Transaction id
and server login details (old server and new server), and I'll
do for you all the steps below (except of hosting accounts migration) . |
|
|
Below you can find instruction to migrate ASSP 1.x and ASSP 2.x
Requirements - You have moved hosting accounts from
old server to new server using WHM/cPanel .
1)
email
me and provide me OLD server ip and NEW server ip . I'll reply you when
your ASSP Deluxe license will be updated
(usually in 12/24 hours). There is no fee to change your
licensed server ip.
When the new server ip will be licensed follow these steps ;
2) install ASSP Deluxe for cPanel (how
to) in the new server, follow carefully all the
post installation steps ; once you have completed this step and all
is working correctly (ASSP 1.x is running) in your new server execute
this
# mkdir /usr/local/assp/old
Now rsync from old to new server all your
old ASSP folder in /usr/local/assp/old ; you can do/rsync it
in this way ; execute this in your
old server , and
replace 209.xx.xx.xx with your new server ip and 22 with your new
server ip SSH port.
Execute this in old server
# rsync -av -L -e "ssh -p 22" /usr/local/assp root@209.xx.xx.xx:/usr/local/assp/old
When the rsync will be completed , in your new server install mc
(midnight commander) in this way ;
# yum install mc
Now STOP ASSP in your new server using your ASSP WHM and
execute mc ( # mc ) and open /usr/local/assp/old/assp in left window ( cd
/usr/local/assp/old/assp ) and /usr/local/assp ( cd /usr/local/assp )
in right window ( you can switch left/right windows using TAB ) ; now
copy (using F5) from /usr/local/assp/old (left window) to /usr/local/assp (right
window)
following folders ;
overwrite files and folders if asked
/usr/local/assp/spam
/usr/local/assp/notspam
/usr/local/assp/discarded
/usr/local/assp/okmail
/usr/local/assp/files
/usr/local/assp/errors
and following files
/usr/local/assp/persblack
/usr/local/assp/spamdb
/usr/local/assp/whitelist
now open /usr/local/assp/old/assp/deluxe in left window ( cd
/usr/local/assp/old/assp/deluxe ) and /usr/local/assp/deluxe ( cd
/usr/local/assp/deluxe ) in right window ( you can switch left/right windows
using TAB ) ; now copy (using F5) from /usr/local/assp/old/assp/deluxe
(left window) to /usr/local/assp/deluxe (right window)
following files ;
/usr/local/assp/deluxe/ignore_whitelistedip.txt
/usr/local/assp/deluxe/dmfile
/usr/local/assp/deluxe/email_warnings
/usr/local/assp/deluxe/warning_ignore
/usr/local/assp/deluxe/whitedomains
/usr/local/assp/deluxe/custom_assp_local_domains
/usr/local/assp/deluxe/custom_assp_local_email
/usr/local/assp/deluxe/custom_assp_local_ips
/usr/local/assp/deluxe/no_auto_settings
Now you can remove /usr/local/assp/old/ in this way
# rm -fr /usr/local/assp/old
All data is migrated , now you can START ASSP 1.x
Requirements : you should have a working ASSP 2.x in old server
your new server should have requirements to install ASSP 2.x
you already moved hosting accounts from
old server to new server using WHM/cPanel .
-
email
me and provide me OLD server ip and NEW server ip . I'll reply you when
your ASSP Deluxe license will be updated
(usually in 12/24 hours). There is no fee to change your
licensed server ip.
When the new server ip will be licensed follow these steps ;
- install ASSP Deluxe for cPanel for ASSP 1.x (
HOW TO ) in the new server
and follow carefully all the
post installation steps ;
In the ASSP 1.x HOW TO
you must execute all step between [ M2_start
] and [ M2_stop ] . You must skip and
not execute all steps between [ M2_stop
] and [ M2_start ] (related to custom
perl installation) .
- At this point you should have ASSP 1.x working and installed
correctly (spambox, scoring mode ON, SSL setup as per post installation
steps). If your ASSP 1.x is running correctly, you can now follow
the ASSP 2.x upgrade here and stop
the ASSP 2.x upgrade when you reach the MYSQL SETUP step , do not
setup MYSQL for now .
Now open ASSP WHM interface in your old server, open MySQL setup ,
and disable MySQL for your ASSP.
Now in your new server execute this
# mkdir /usr/local/assp/old
Now rsync from old to new server all your
old ASSP folder in /usr/local/assp/old ; you can do/rsync it
in this way ; execute this in your
old server , and
replace 209.xx.xx.xx with your new server ip and 22 with your new
server ip SSH port.
Execute this in old server
# rsync -av -L -e "ssh -p 22" /usr/local/assp root@209.xx.xx.xx:/usr/local/assp/old
When the rsync will be completed , in your new server install mc
(midnight commander) in this way ;
# yum install mc
Now STOP ASSP in your new server using your ASSP WHM and
execute mc ( # mc ) and open /usr/local/assp/old/assp in left window ( cd
/usr/local/assp/old/assp ) and /usr/local/assp ( cd /usr/local/assp )
in right window ( you can switch left/right windows using TAB ) ; now
copy (using F5) from /usr/local/assp/old (left window) to /usr/local/assp (right
window)
following folders ;
overwrite files and folders if asked
/usr/local/assp/spam
/usr/local/assp/notspam
/usr/local/assp/discarded
/usr/local/assp/okmail
/usr/local/assp/files
/usr/local/assp/errors
/usr/local/assp/mysql
and following files
/usr/local/assp/HMMdb
/usr/local/assp/persblack
/usr/local/assp/spamdb
/usr/local/assp/whitelist
now open /usr/local/assp/old/assp/deluxe in left window ( cd
/usr/local/assp/old/assp/deluxe ) and /usr/local/assp/deluxe ( cd
/usr/local/assp/deluxe ) in right window ( you can switch left/right windows
using TAB ) ; now copy (using F5) from /usr/local/assp/old/assp/deluxe
(left window) to /usr/local/assp/deluxe (right window)
following files ;
/usr/local/assp/deluxe/ignore_whitelistedip.txt
/usr/local/assp/deluxe/dmfile
/usr/local/assp/deluxe/email_warnings
/usr/local/assp/deluxe/warning_ignore
/usr/local/assp/deluxe/whitedomains
/usr/local/assp/deluxe/custom_assp_local_domains
/usr/local/assp/deluxe/custom_assp_local_email
/usr/local/assp/deluxe/custom_assp_local_ips
/usr/local/assp/deluxe/no_auto_settings
Now you can remove /usr/local/assp/old/ in this way
# rm -fr /usr/local/assp/old
All data is migrated , now you can START ASSP 2.x and complete the
upgrade procedure from MySQL Setup .
How to
allow a remote MX ? ( #36 )
If you have some user using remote MX , you should put the ip
address of their remote mx server on ISP/Secondary MX Servers .
Open the "ASSP web interface" go to "Relaying menu" , "ISP/Secondary MX
Servers" , and click edit file , then add the remote ip and Save.
NEW : with ASSP Deluxe 2.8.0 and above, the cronjob
ex_localdomains.php take care of this automatically .
Does ASSP send a daily email report to each email account with a list of
blocked emails and options to deliver, whitelist, blacklist etc. like
Barracuda does?
Yes it's possible, you can set this by setting
ASSP Web Interface > File for Blockreportrequest (BlockReportFile)
I messed up my assp.cfg what to do now ? ( #08 )
 |
With ASSP Deluxe
4.1.5 and above versions you can
find latest 30 working assp.cfg
in /usr/local/assp/backup_cfg .
Before restoring one of them stop ASSP
using your ASSP WHM interface . |
|
|
STOP ASSP using ASSP WHM 6.x . Now from console execute this
# rm -f /usr/local/assp/assp.cfg
# cd /usr/local/assp;wget -r -nH --cut-dirs=10 http://www.grscripts.com/196/assp.cfg
Now execute following command replacing
yourhostname with your hostname .
replace "email@youremail.com"
"root@yourhostname"
-- /usr/local/assp/assp.cfg
Now START ASSP using your ASSP WHM INTERFACE.
Finished , now you have reset your assp.cfg and all should work correctly.
I'm using "ASSP scoring mode ON" but I
am still receiving some spam .... (#A86)
If few spam is passing , first be sure you followed the
post installation steps .
If spam is still passing after
this step , copy the spam (email header included) , and paste it
inside a myspam.txt file ; repeat this step for min 10
received spam . Now save the file, compress/zip the myspam.txt
file and send it to
this email
Is the /spambox folder created automatically (or does it need to be added by
the end-user)?
imap spambox
In user email client and Horde webmail the /spambox imap folder is created
automatically after the first received spam.
In Squirrel and Roundcube the /spambox imap folder should be subscribed
after the first received spam to make it visible , OR the user can
wait max 24 hours after the first received spam and it (/spambox)
will be created automatically using the ex_localdomains.php cronjob.
spambox pop3 collector
ASSP will collect spam in user inbox immediately after the first received
spam
How can
we whitelist email address or a full domain name @domain.com ? [#51]
The user
1) Using the ASSP
email
interface : the user should send an email to
assp-white@clientdomain.com
(to whitelist an email)
To add email addresses to the whitelist, your customer (local user) should create a
message to assp-white@clientdomain.com .
He can either put the
addresses in the email subject of the message.
If your customer want whitelist a domain name he should enter
*@domain.com
(where domain.com is the domain name to be whitelisted) in the
email subject . He can enter also a list of domain or email to be whitelisted .
The email should be sent using
smtp auth ON (email client) ; after few seconds the user should receive
an
ASSP email notification.
2) each time your user send an email to someone , the email will be
whitelisted automatically, so
the user should never reply to a spammer.
The server admin
The server admin can whitelist full domain
name (@domain.com) and/or email addresses.
As admin open the
ASSP WEB INTERFACE (port 55555), Whitelisting menu ,and you have a
several options and especially ;
Whitelist Domains and ips
set Regular Expression to Identify Non-Spam
 |
NOTES
A) If after whitelisting an email
or domain , you still not receive the
email from remote sender , it means the
remote sender ip address has been
collected in the IP Blocking (ASSP Web
interface > IP Blocking >
denySMTPConnectionsFrom or
denySMTPConnectionsFromAlways ip
collections) . In this case if you know
the sender ip address (you can grep the
ASSP log to find the sender ip address)
you can allow the ip using ASSP WEB
interface > Whitelisting menu >
whiteListedIPs ; if you don't know
the sender ip address simply go in your
ASSP WHM and click FLUSH IP BLOCKING.
B) You should never
whitelist a local domain or local email
using your ASSP Web Interface. ASSP
already fully allow local
domain and email . If ASSP is blocking a local sender please
read this.
C) The ASSP whitelist file is
stored on /usr/local/assp/whitelist. You
should not edit this file since it's
generated automatically.
You can enter whitelist email or domain also using ASSP
web interface > Whitelist > whitedomains |
|
|
mailing list email extraction (mailman problem)
The /user/local/assp/deluxe/assp_local_email file contains all
your local/server email (email forwarders and mailing lists included) . If
some mailing listing is not working (ie. test@youdomain.com) and you cannot
find test@youdomain.com on your assp_local_email flat file , execute this to
fix the problem .
# /scripts/fixmailman
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php
Antivirus and attachments [#41]
With default ASSP antivirus/attachment configuration
following attachments are not allowed (cannot be
received)
ad[ep]|asx|ba[st]|chm|cmd|com|cpl|crt|dbx|exe|hlp|ht[ab]|in[fs]|isp|js|jse|lnk|md[abez]|mht|ms[cipt]|nch|pcd|pif|prf|reg|sc[frt]|sh[bs]|vb|vb[es]|wms|ws[cfh]
Please note that ad[ep] means .ade and .adp , ba[st] means .bas and
.bat and so on ...
You can receive these attachments only if they
are compressed using .zip
Infact if anyone try to send your assp server above attachments the sender
receives following error
500 These attachments are not allowed -- Compress
before mailing.
Following extensions are allowed
ai|asc|bhx|dat|doc|eps|gif|htm|html|ics|jpg|jpeg|hqx|pdf|ppt|rar|rpt|rtf|snp|txt|xls|zip
You can change these settings using your ASSP Web Interface as required
( attachment menu ).
I have various emails in my OKMAIL collection. They all have low X-ASSP SCORE and low Bayesian confidence.
A lot of spam is passing due to this reason.
#spam_passing
It happens if your Bayesian spam database (and HMM database in ASSP v2) is
not efficient. You can fix the problem forwarding all spam found in inbox to
assp-spam@yourdomain.com and all good email found in spambox to
assp-notspam@yourdomain.com .
Or you can open your ASSP WHM > open the OKMAIL collection > and correct
(move to SPAM) all the spam found in this collection .
If the two options
above are not possible you may follow this other way .
If you are
using ASSP v1
- Open ASSP WHM > Score Settings Set the
MessageScoringUpperLimit to 45 and
Bayesian to 44
If you are using ASSP v2
- Open ASSP WHM > Score Settings Set the
PenaltyMessageLimit to 50-53 , Bayesian to 15-25
and HMM to 40-43
Now add this cron in your ASSP Deluxe root
cron list ( # crontab -e ) . You must
have Deluxe version 9.3.1 or above .
0 */6 * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/build_spamdb.php
this cron will check your /okmail collections
using multiple RBLs ,Pyzor and Razor checks, and it will correct errors moving
the email in /errors/spam collection.
Day by day this cron
should improve performance of your Bayesian (and HMM if you have ASSP v2) spam
database.
If the steps above will not reduce spam passing after some day
of usage please try this addictional step ; go to console and execute this
# touch
/usr/local/assp/deluxe/rbl_pb_settings_manual
Now open your ASSP GUI ,
go to DNSBL menu and set DNSBL Neutral
(rblnValencePB) to 45 and DNSBL
Failed (rblValencePB) to 50.
 |
Following
instructions are valid if have Deluxe
version 9.3.1 or above
Pyzor
build_spamdb.php will try to use
Pyzor too if available.
build_spamdb.php will check existence of
/usr/bin/pyzor and it will try to
connect to Pyzor using UDP and TCP port
24441 . If these 2 checks will fail ,
build_spamdb.php will not
use Pyzor.
If you execute
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/build_spamdb.php
from console you should receive this
message, if all Pyzor checks are working
correctly.
Pyzor checks
available [ OK ]
If you
do not see the message ago be sure the
firewall is not blocking port 24441 and
be sure Pyzor is installed in
/usr/bin/pyzor .
How to install Pyzor
if it's not available in your server.
1) automatically , by executing this
from console#
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php
install_pyzor=yes
2) compile it using docs available at
Pyzor
Razor
build_spamdb.php will try to use
Razor
too if available. build_spamdb.php will
check existence of
/usr/local/bin/razor-check and it will
try to connect to Razor using TCP port
2703. If these 2 checks will fail ,
build_spamdb.php will not
use Razor.
If you execute
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/build_spamdb.php
from console you should receive this
message, if all Pyzor checks are working
correctly.
Razor checks
available [ OK ]
If you
do not see the message ago be sure the
firewall is not blocking TCP port 2703
and be sure Razor is installed in
/usr/local/bin/razor-check and
/usr/local/bin/razor-report .
How to
install Razor if it's not available in
your server.
1) automatically , by
executing this from console
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php
install_razor=yes
2) compile it using docs available at
Razor
|
|
|
What
is the delaying filter ? #87A
Note : this explanation could be found also in the ASSP Deluxe cPanel
user frontend (HELP
button)
Delaying is a method of blocking big
amounts of spam at the mailserver level .This
method is also called "Greylisting".
Delaying works on the idea that a correctly configured SMTP server
will always attempt re-delivery of an email message if it gets a soft
failure. How does it work exactly ? When someone send an email to our server (and
you or your client have the delaying filter enabled), ASSP will
return a 451 error (soft failure) .
If the sending mail server is correctly configured it will reattempt
to deliver the email in X number of minutes. (it depends upon its configuration) . If
the sender mail server waits and redelivers , the triplet (email
address, domain,IP) gets whitelisted by ASSP (delaying whitelist) and you'll
receive the email .
When will you receive the email ? If the mail server is configured
correctly you should receive the email after min 5 minutes (default
embargo time) and max 28 hours (default
wait time) . If the remote mailserver doesn't reattempt the
deliver (and the spammers usually do not reattempt the deliver) the
email will be rejected after the wait time (28 hours) and you'll
never receive the email message.
May I lose some valid email ? Only if the sender (mailserver sender) is
not configured to reattempt the deliver .
reasons not to use
- its behavior could create some confusion to unexperienced users
- SPAM SCORING is more efficient than delaying
filter, some spam could pass
- the email rejected due to delaying filter cannot be retrieved using the SPAMBOX@
plugin.
There is no spam collection using delaying
filter
- your Bayesian (and HMM) database can't be populated
using delaying.
reason to use
-
very useful to reduce email traffic , for example if your server is under a
huge spam attack
Using the "ASSP Email interface" .
The "ASSP Email inteface" is a powerful ASSP feature which permits to
add or remove email to the Whitelist, report Spam, or false-positives
improving the Bayesian filter. For example the "R" button that
you can see on the "ASSP deluxe for cpanel" log pages uses the
ASSP email
interface to report false positives.
Some user could report you that is not able to forward (forward as
attachment) a spam message to assp-spam@clientdomain.com .
ASSP email interface (assp-spam@clientdomain.com assp-white@clientdomain.com
and so on) accepts reports only if the sender client uses smtp
auth on (only from smtp authenticated users).
Horde, Squirrel and Roundcube are automatically configured by ASSP Deluxe for
cPanel to use the ASSP email interface (thanks to Steve Hollar for
Horde and Squirrel tweaks).
We are getting the following error "Bayesian spam
database is small or empty: '/usr/local/assp/spamdb'"
This error happens on the first hours of ASSP usage . It's normal since ASSP
has still to build it's database.
Does ASSP support SNI ?
ASSP V1
If you enabled TLS/SSL in ASSP WHM > SSL MENU
your customers can use SNI in their SMTP ( the
SNI SSLs are all stored in /var/cpanel/ssl/domain_tls/and you can find a list of
all of the SNI enabled domains in the dovecot configuration
in /etc/dovecot/sni.conf ).
However if your customers use SMTP
mail.customerdomain.com with an SSL/TLS port they'll receive a "Domain warning" in
the Certificate ( which can be skipped ) .
If your customers do
not want receive a "Domain warning" in the certificate, they should use the
server certificate and SMTP which was setup in ASSP WHM > SSL MENU
.
ASSP V2
YES, ASSP v2 fully supports SNI,
you can enable SNI globally or per domain using your ASSP WHM > SSL MENU
interface
Does ASSP can score
based on TLDs ?
Yes, you may use 'bombSenderRe'
with a negative (or positive) weigth - like:
\.no$=>-10
\.me$=>+5
How to find and release good messages ? How
does work spambox@ ?
Clients have been asking - how do they retrieve
legitimate messages that have been rejected by ASSP ?
First of all you should activate spambox@ using the
assp WHM web interface.
Then to release a good message your client should use spambox @ pop3 ; or
your client can check the /spambox imap folder to read all received spam
(and forward as attachments false positives to
assp-notspam@clientdomain.com)
You , server admin , should activate the ASSP Deluxe for cPanel
SPAMBOX@ plugin using WHM assp web interface.
If you (server admin) activate the assp deluxe for cPanel SPAMBOX@
plugin
the SPAMBOX@ plugin redirects all rejected spam(*) to
spambox@clientdomain.com , only if the client creates a
spambox@clientdomain.com email AND always to the /spambox imap
subfolder of each email user .
Some example
a) Using
spambox@domain.com pop3
If your client creates
spambox@domain.com (pop3 account) all spam sent to @domain.com
will reach
spambox@domain.com .
Now if the client login on his pop3 account
spambox@domain.com he can see all the spam which reached his domain name
@domain.com . If he see a false positive (good email) he can forward (or
forward as attachment , better) the email to the destination contact , for
example
test@domain.com .
He can check
spambox@domain.com such as any other email account on his server , using
his email client , horde or squirrel.
b) Using imap
ASSP deluxe spambox@ sends all the received spam also to each account on
your server (exactly to the /spambox imap folder of each email account).
For example if the owner of
test@domain.com checks the email using imap (using an imap email client
such as Thunderbird or webmail Horde), if he received some spam , he can
find the spam on the /spambox imap folder. If no /spambox imap folder
exists it means that
test@domain.com received no spam . If the owner of
test@domain.com see a valid email on /spambox he can
forward as attachments this email
to
assp-notspam@domain.com , and it will be never blocked. Or he can
simple reply to the email , and assp will never block it again.
3) Using webmail
Using webmail Horde , Squirrel , and
Roundcube the user can check the spam reading the /spambox folder.
Horde detects the /spambox folder automatically (after the first spam
received) . On Squirell and Roundcube the user should subscribe
the /spambox imap folder ; since ASSP WHM 6.0.0 the folder /spambox in
Squirell and Roundcube can be subscribed automatically each 24
hours after the first collected spam . If the owner of
test@domain.com see a valid email on /spambox he can
forward as attachments this email
to
assp-notspam@domain.com , and it will be never blocked (or he can
simple reply to the email , and assp will never block it again).
Using Squirrell the user can also move to INBOX the false positive contained
on /spambox (!)
Is my Antivirus clamAV working fine ?
You can execute 2 checks ;
1) restart clamAV from command line while ASSP is running
/usr/local/cpanel/scripts/restartsrv_clamd
The line
Starting clamd: [ OK ]
should not report errors.
2) Open the ASSP Web interface (port 55555)
Click on "info and stats" and click on "Perl Modules"
You should see a line like this
File::Scan::ClamAV
1.8
CPAN
If instead of ClamAV version you see an error your clamd
antivirus is NOT working .
Do I need to create email addresses assp-white@client.com ?
NO . ASSP will parse these emails automatically . It's the
ASSP
Email Interface feature ; if you followed corrently the HOW TO the Email
Interface is enabled by default .
Only SMTP authenticated users will be able to use the ASSP Email
Interface .
move.php #move
In ASSP Deluxe 6.0.7 and above version there is a console utility
to search, move or delete email messages in your Bayesia/HMM collections .
Following move.php commands are available
search=[search_string]
moveto=[spam][notspam][okmail][discarded][delete]
where=[spam][notspam][okmail][discarded]
how to use it
Suppose ASSP collected incorrectly various spam email with subject (or body
content) "buy this viagra soon" in /okmail folder and you
want move all them in /spam folder . You should execute this
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/move.php search="buy this viagra soon"
where=okmail moveto=spam
when you terminate to move email , you can run rebuildspamdb using your ASSP
WHM .
Should I forward spam collected in spambox to
assp-spam@mydomain.com ?
NO , you should never forward spam in spambox to assp-spam@ . It useless
, ASSP already know it's spam .
The spambox exists for one important reason ;
- collect all the spam and check if there is some good
email inside
If you do not want collect spam in spambox simply disable spambox for your
account . ASSP send/collect spam in your spambox (if you enabled it) because you
want see if there is some good email inside , only for this.
So only if you see a good email in
spambox you should forward as attachment to assp-notspam@
and only if you see spam in inbox you
should forward as attachments to assp-spam@
Adjustments to your ASSP WHM > Score Settings page are required if
1- too much spam is going to inbox
2- too much good email are going to spambox
If 1 and 2 and are not happening there is no reason to adjust your ASSP
scoring settings.
I have a customer which would receive each
day the asspblock@ report for all blocked email in his domain customerdomain.com
to his email xyz@gmail.com , how to do that ?
#ablock
Open ASSP web interface > Blocking reports menu > File for Blockreportrequest
(BlockReportFile)
click edit and enter this
*@customerdomain.com=>xyz@gmail.com
ASSP will send o xyz@gmail.com the asspblock@ report for all email
blocked sent to customerdomains.com .
What does it mean "strictly denied by
denySMTPConnectionsFromAlways or droplist" ?
If you see something like this in ASSP maillog ( /usr/local/assp/maillog.txt
)
Jan-21-10 19:17:08 65.11.11.11:19231 strictly denied by
denySMTPConnectionsFromAlways or droplist:
65.11.11.11
If you receive an error like above it means find_abusers.php collected the ip
65.11.11.11 in bad list (denySMTPConnections and/or
denySMTPConnectionsFromAlways) , so even if you whitelisted the sender email
ASSP knows that the ip 65.11.11.11
MUST be blocked .
If you want allow this ip to pass, simply open ASSP web interface ,no processing
menu , No Processing IPs* (noProcessingIPs) , enter the ip and save. Now the ip
address will pass .
How to avoid the problem in the future ? If you grep 65.11.11.11 in the old ASSP
logs you can understand why find_abusers.php collected this ip and you can apply
more relaxed settings to your find_abusers.php bad ip collection in case.
If you are waiting an email from a remote sender but there is no trace of the
email AND of the sender IP address in ASSP/exim log , it means that something
else is blocking the sender (firewall for example).
If you suspect the sender ip is blocked and you have no idea which is the sender
ip you can
simply go in your
ASSP WHM and click FLUSH IP BLOCKING
to clean the bad ip collections .
How to
edit the ASSP whitelist ? ( #74 )
There is no way to see/edit the whitelist used by ASSP using ASSP Deluxe
or ASSP web interface because the list
is created dynamically by ASSP. For example each time you send an email ,
ASSP automatically whitelist each email destination .
Also each time you use assp-notspam@ (and assp-white@ of course) , assp
whitelist the emails .
For this reason the whitelist file should not be edited , but you should act
with it using assp-white@ assp-notwhite@ assp-notspam@ and so on... . As
admin you can also use the whitelist menu on ASSP web interface of course.
If you want only see the whitelist
# cat /usr/local/assp/whitelist
for the reason explained above I do not suggest you to edit the whitelist
file.
How to disable ASSP temporarly ?
( #20 )
If you need to disable
ASSP temporarly and you want
use only EXIM (standard cPanel usage)
there is no need to
uninstall ASSP you should follow these steps ;
If you have ASSP WHM 7.x or above you should
simply click ASSP STOP
in your ASSP WHM

You will receive the message above. If you click the "click
HERE" link , ASSP will be fully disabled
and EXIM will be unproxied from ASSP , normal cPanel usage
with ASSP disabled.
You will receive this message

EXIM is now working without ASSP , normal cPanel usage.
To re-enable
your ASSP
Simply click START ASSP , EXIM will be reconfigured correctly and ASSP
restarted .
ASSP professional spam filter
I'm receiving "Server replied: 111 Can't open SMTP stream" using
Squirrel/Horde
The problem is not related with ASSP . You should find the problem on your
firewall. Be sure you have port 25 TCP IN/OUT and 125 TCP IN opened .
Also your alternative port (26 i.e.) should be opened.
My client domain cannot receive
email and it's receiving a "relay attempt blocked" error. ( #57 )
Check if your client domain is listed correctly on /etc/localdomains
(or if it's listed incorrectly on /etc/remotedomains) .
If no, add the
client domain name to your /etc/localdomains file (#nano /etc/localdomains)
. Restart ASSP using the WHM assp web interface. It fixes the problem. If
the problems does not fix check also if the client main domain is
listed on /etc/trueuserdomains .
How to
bypass ASSP ? ( #56 )
if you want disable fully ASSP for a local or remote domain name or
email you should use noprocessing menu in ASSP .
If you are using ASSP
v1 :
To bypass
a local domain or email
open ASSP Web interface > no processing menu >
and add your domain to "No Processing Addresses* /(noProcessing) " ,
Save .
To bypass a remote domain or email
If you want fully disable ASSP for a REMOTE domain sender
open ASSP Web interface > no processing menu >
and add your domain to "No Processing Domains* (noProcessingDomains)",
Save.
If you are using ASSP
v2 :
To bypass a local or remote domain or email
open ASSP Web interface >
No Processing - IP's, Domains, Addresses and Limits menu >
and add your domain to "No Processing Addresses* (noProcessing) " ,
Save .
note : If you register TO addresses here (so
local domains or local email), all recipients
for a single mail must be marked as noprocessing to flag the mail as
"noprocessing". If you want be sure the TO address will be bypassed in each
situation you may use
Regular Expression to Identify No Processing Mail*
(npRe) .
Advanced usage : also the asspof@ and asspon@ are available in the
ASSP email interface menu (ASSP v1 and v2).
spambox not working (cagefs restriction)
56bb
note : this problem could happen only in old Deluxe piping
spambox, latest ASSP Deluxe versions does not have this problem. Latest ASSP
Deluxe versions are fully compatible with Cloudlinux and cagefs.
If you installed the ASSP Deluxe spambox but it's not working, and you
are receiving following error in EXIM maillog
2014-01-01 18:33:42 1XoKwQ-0049HL-9g => |/usr/local/assp/deluxe/piping_b.php
(spammaster@spamxyz.us) <spammaster@spamxyz.us>
R=virtual_aliases_nostar T=cagefs_virtual_address_pipe
you can fix the cagefs restriction in two ways .
1 You
may add spamxyz.us in your cagefs
exclude list using ASSP WHM > Plugins > CageFS.
2 You may add /usr/local/assp
and /home/user ( replace
user with the spamxyz.us username! ) into
/etc/cagefs/cagefs.mp file, and execute # cagefsctl --remount-all
After one of these two steps above email spambox piping will start to work
properly. If solution 2 does not work uses solution 1 or viceversa.
ASSP restarts often , what to do ? ( #10 )
It should not happen if you are using ASSP 1.9 or above versions . If it happens , be sure you are running
latest versions of each scripts (using assp WHM web interface) and check if
your server is under a ddos email attack.
EXIM restarts often , what to do ?
EXIM restarts are not due to ASSP . You may try executing a cPanel
update .
If after this step EXIM has still problems you can disable temporarly
ASSP in this way
http://www.grscripts.com/howtofaq.html#20 , then open a ticket with
cPanel and ask to investigate your EXIM issue.
Are you running out of disk space on /usr ?
#71O
First of all you can delete all old ASSP logs in this way
cd /usr/local/assp
rm -f *.maillog.txt
If you have still disk space problems you can create a
symlink for /usr/local/assp/spam and /usr/local/assp/notspam
Suppose you want symlink data from /usr/local/assp/spam to /home/spam and
from from /usr/local/assp/notspam to /home/notspam
STOP ASSP using WHM then execute this
# mv /usr/local/assp/spam /home/spam
# mv /usr/local/assp/notspam /home/notspam
# ln -s -f /home/spam /usr/local/assp/spam
# ln -s -f /home/notspam /usr/local/assp/notspam
Now START ASSP using WHM .
Done. You should have fixed your disk space problems on your /usr
partition.
I have an user which
does not use imap , which are alternative ways
to check spam without imap ?
- DAILY blocked email report , which send a
list of blocked email in the inbox each 24
hours.
- Your customer can send an email to asspblock@customerdomain.com to
require a fresh list of all blocked email.
-
Your customer can create a spambox@domain.com pop3 collector which collects
all spam sent to domain.com in
the pop3
spambox@domain.com
- legacy
cPanel way by adding /spam to the email (more info in cPanel >
ASSP , spambox red icon)
ex_localdomains.php ( crow=1 )
ex_localdomains.php creates an updated list of
email/forwarders/domains/subdomains of
your server .
Email are stored on /usr/local/assp/deluxe/assp_local_email , domain names
are stored on assp_local_domains . It executes also some other important
check (i.e. it checks default assp per domain configuration , checks
integrity for spamlovers files , checks if horde,squirrel and mailman are
configured correctly to work with ASSP, other..).
If you add crow=1 to your ex_localdomains.php cronjob
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php crow=1
you may add an email address as a spamlover
using the ASSP Web interface. How it works
Suppose a client ask you to turn off RBL (i.e.) only for one
email. For example he wants that the email
clientemail@domain.com bypasses
the RBL filter ; you should do this
- be sure you are running ex_localdomains.php cronjob with crow=1 (see
above)
- open the "ASSP Web Interface" and open the "SPAM Lover/No
Processing" menu
- go to DNSBL Failures Spam-Lover (which is the RBL filter) click on
edit and add the
clientemail@domain.com to the list .
In this way
clientemail@domain.com will bypass the RBL filter check.
clear_spambox.php ( advanced usage ) ( #09 )
If you are using the spambox@ plugin , mailbox for your client
could grow very fast especially for clients receiving a lot of spam. To
avoid disk usage problems for your clients set following cronjob (you can
run it daily) using "crontab -e" from command line
10 4 * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/clear_spambox.php
By default the cronjob above will run each day , removing @spambox email on
all your accounts older than 7 days . If you want change the default ( 7
days ) you should enter the cron in this way
10 4 * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/clear_spambox.php sday=n
and replace n with your days. For example ...
10 4 * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/clear_spambox.php sday=15
it will remove spambox@ emails older than 15 days on all your server
email accounts.
Other commands which could be added to your clear_spambox.php cronjob
noemail=yes ; it disables cleaning spambox email notifications
sp=yes ;
limitspace=x (x = disk space in Kilobytes)
remdays=x (x = other days to be
removed)
Above 3 commands (sp, limitspace and remdays) should be used/entered at
the same time . At the end of the cleaning work ,
clear_spambox.php checks if disk usage for each already cleaned mail
folder is over your limitspace in kilobytes . If some mail
folder is over the limit it removes other remdays from this spam folder.
nodisabled=yes
If you add nodisabled=yes to your clear_spambox cronjob , all the
users having imap spambox disabled will not be
processed/cleared .
norep=yes
If executes the spambox cleaning without sending the DAILY SPAM REPORT
email
.
noclean=yes
If does not executes the spambox cleaning . The DAILY SPAM REPORT email
will be sent.
/usr/local/assp/deluxe/custom_cleaner
# custom_cleaner
if you create/edit a file /usr/local/assp/deluxe/custom_cleaner
you can add a list of email address (one email per row) . All email added in
this list will be processed with sday=1 ( It's useful for email which
would leave the spambox very small ).
ASSP cpanel antispam
update_email.php (commands for avanced
users)
nohup=yes
If you add nohup=yes to your update_email.php cronjob ,
update_email.php does not store "number of ASSP smtp connections"
on ASSP STATUS CHART
Why am I receiving 2 or 3 copies of "upgrade
notification email" ?
One email is sent to email specified in WHM > Basic cPanel & WHM Setup
One email is sent using the cex=email value specified in
ex_localdomains.php cronjob
One email is sent to the email contact specified in ASSP Web interface >
EmailAdminReportsTo
If you want receive always a single email , remove cex= from
ex_localdomains.php if you are using it
and replace it with cc=your_preferred_email , and you will receive always a
single email to your cc= email .
i.e.
*/59 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php cc=youremail@yourdomain.com
Email I send out gets bounced with ip reputation problems #76A
0 - be sure there is no outgoing spam activity in your WHM
email queue.
1- check if your server ip is blacklisted in some RBL list and ask
an ip removal ( you can check
here
i.e. )
2- remember that ASSP deluxe offers various ways to protect you
against spam exiting from your server
listed here
3- after you fix the first point for a better reputation
apply this
http://www.grscripts.com/howtofaq.html#840
how to
set a postmaster@ and abuse@ email for all my clients
to fix RFC errors ?
(#20b)
If you want set a working postmaster@ and abuse@ email for
each domain , subdomain , addon domain or parked domain
on your server , you may follow the procedure explained below .
First remove from "no processing , spamlover, whitelist" or from any
other ASSP web interface menu,
each abuse@ and postmaster@ value.
Now simple execute this from console
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/fix_abuse_postmaster.php
The scripts will create 2 forwarders for each domain , subdomain , addon
domain or parked domain on your server.
1) abuse@domain.com redirected to user_name@domain.com
2) postmaster@domain.com redirected to user_name@domain.com
If you want forward all the email sent to abuse@ and postmaster to your
preferred server email (your own postmaster) for example
abuse@myserver.com (for abuse@) and post@myserver.com (for
postmaster@) you should execute this
instead
# /usr/local/cpanel/3rdparty/bin/php-cgi /usr/local/assp/deluxe/fix_abuse_postmaster.php
forwardto=abuse@myserver.com forwardto2=post@myserver.com
1) abuse@domain.com will be redirected to
abuse@myserver.com
2) postmaster@domain.com will be redirected to
post@myserver.com
Note :
1) the script will not create the forwarder if a pop3 or
forwarder abuse@ or postmaster@ email already exists for that domain.
2) If you want remove all postmaster@ and
abuse@ rows from your /etc/valiases/* files you should execute this
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/fix_abuse_postmaster.php clean=yes
Set a cronjob
If you want be sure that also new domain names will be set with abuse@
and postmaster@ you may set a cronjob
(such as other ASSP Deluxe cronjobs put
it between MAILTO="" and MAILTO="root" ).
For example the command below will execute the cron each 12 hours ,
10 */12 * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/fix_abuse_postmaster.php
credits : idea of Elie P. by
webdomain.com
How to preserve usage of my
/etc/cpanel_exim_system_filter ? #56d
open your ASSP WHM > Automation settings and set OFF exim_systemfilter
How to detect root@hostname outgoing spam
activity ? #56c
With ASSP Deluxe 5.4.3 and above versions in ex_localdomains.php
is able to detect huge outgoing email activity sent by
root@yourhostname .
If root@yourhostname send 500 email (a) , you will receive a
detailed email warning .
ex_localdomains.php
analyzes latest 50000 (b) lines of your exim_mainlog .
(a) this can be customized adding hst=your_value to to your
ex_localdomains.php cronjob
(b) this can be customized adding hst_lim=your_value to to your
ex_localdomains.php cronjob
How to detect possible SPAM script activity which is exiting from my
server using a script ? (#56b)
With ASSP Deluxe 3.1.7 and above versions in ex_localdomains.php
and find_abusers.php has been added code to detect possible huge SPAM activity which is exiting
from your server using a script (perl,php..other). In case of detected SPAM
activity you will receive an email warning or you may change
permissions on the folder which is sending the email .
1) OUTGOING SPAM ACTIVITY DETECTOR using ex_localdomains.php
If any user in your server send 400 email (a) using a script and
the exim queue value is greater than 5 (b), you will receive a
detailed email warning with the script location which is sending the email. ex_localdomains.php
analyzes latest 200000 lines of your exim_mainlog .
The user will not be blocked automatically , however you can
investigate and block him if required.
The email will be sent to the email contact you have set on your ASSP WHM .
If you want set a custom email you add
cex=custom@email to your
ex_localdomains.php cronjob (only with ASSP Deluxe 3.7.4 or
above)
(a) this can be customized adding lim_email=your_value to to your
ex_localdomains.php cron
(b) this can be customized adding lim_queue=your_value to to your
ex_localdomains.php cron
This feature is enabled by default. If you would disable this
functionality you should add nsp=yes to your ex_localdomains.php
cron , in this way
*/59 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php nsp=yes
2) OUTGOING SPAM ACTIVITY DETECTOR using find_abusers.php
#88c
By default if you execute find_abusers.php from console
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/find_abusers.php
you may receive something like this
Email sent from your server using a script : looking
for more than 10 email on latest 200000 lines of your exim_maillog
=============================================
82 = > /home/chat/public_html/preloginchat4
26 = > /home/harleyb/public_html/condo/yabb
By default , as explained on the title above (Email sent from your
server using a script...) , find_abusers.php analyzes latest 200000
( ex= ) lines of your exim_maillog looking for clients which sent
more than 10 ( lim_email= ) email using a script.
You will NOT receive an email notification such as with
ex_localdomains.php . It will only
show you the results on your console (such as in the example above).
ex=n default value 200000 ,can be customized adding ex=your_value to your
find_abusers.php
lim_email= default value 10 , can be customized adding lim_email=your_value to your
find_abusers.php
BLOCKS and avanced features
If you add bl=1 to your find_abusers.php cronjob , find_abusers.php will
check if latest 5 ( lu= ) new created
hosting accounts sent more than 600 email
( lx= ) . In this case (if bl=1 has been set) the script location will be
chmoded 000 and you will receive an email warning.
The email will be sent to the email contact you have set on your ASSP WHM.
If you want set a custom email you add
cex=custom@email to your find_abusers.php
cronjob (only with ASSP Deluxe 3.7.4 or above)
This is useful to
block spammers which open new accounts only to send spam after few days/hours .
lu=n default value 5 , can be customized adding lu=your_value to your
find_abusers.php cronjob
lx=n default value 600 , can be customized adding lx=your_value to your
find_abusers.php cronjob
* If you add demo=1 you will only receive the email warning and chmod 000 will
NOT apllied (demo mode)
*
If you would check also some suspicious account add the username to
/usr/local/assp/deluxe/checkabuser (one user per line)
*
If you would ignore some account add the user to
/usr/local/assp/deluxe/checkignore (one user per line)
These customized values can be added togheter with your
find_abusers.php values used for bad ip collection.
For example you may use also lu=0 and enter only your suspected users
on /usr/local/assp/deluxe/checkabuser
You may report bug or suggestions
here . Thank you!.
I received the "ASSP Deluxe : possible outgoing
SPAM activity detected" email and this was very helpful
to detect hacked accounts which was sending outgoing spam. What is the best
way and fastest way to delete outgoing spam emails - generated from the
hacker script ?
open your ASSP WHM , and click "EMAIL QUEUE FINDER" , at this point
you should see the outgoing email in the list, now click the "Delete ALL"
button . This is the best and selective way
Is there a way to ignore an user in the "ASSP Deluxe : possible outgoing
SPAM activity detected" email.
#A49
If you have ASSP Deluxe 7.1.6 or above yes . Simply execute this
echo "username" >> /usr/local/assp/deluxe/ignore_spamout
and the username will be ignored . You can add other usernames in the way
above.
If you need to remove an user you can use your preferred editor
(vi,nano..)
nano /usr/local/assp/deluxe/ignore_spamout
and remove the username from the list.
Other ways to block outgoing SPAM (local senders)
#A44
With ASSP 1.9 you have other ways to block outgoing spam (SPAM
exiting from your server) , over the way you should already know
using using
ex_localdomains.php and find_abusers.php
http://www.grscripts.com/howtofaq.html#56b
If you want activate antispam protection for local senders you may
set
ON the following parameters below
which are disabled by default .
ASSP Web Interface => Message Scoring > Bayesian
for Local Messages (bayslocalValencePB)
ASSP Web Interface => Bayesian menu > Bayesian Check on Local
Senders (BayesLocal)
ASSP Web Interface => Regex/Bomb menu => Do Black Regular Expressions
Checks for Local Messages (blackReLocal)
ASSP Web Interface => ClamAV and FileScan > Scan Local Senders
(ScanLocal)
ASSP Web Interface => Validate sender > Check External Sender
for Local Address (DoNoValidLocalSender)
You can set size limits here ;
ASSP Web Interface => smtp session limits > Max Size of Local Message
(maxSize)
ASSP Web Interface => smtp session limits > Max Real Size of Local
Message (maxRealSize)
You can set outgoing limits here ;
ASSP Web Interface => Control Outgoing menu => Local Frequency
Interval (LocalFrequencyInt)
ASSP Web Interface => Control Outgoing menu => Local Frequency Recipient
Number (LocalFrequencyNumRcpt)
Note :
if the email are sent via
socket/sendmail they will NOT be checked by ASSP. |
Daily Blocked email report
#dr
From ASSP WHM 7.7.8 you will find a new
feature in your ASSP WHM interface, DAILY BLOCKED EMAIL . The "DAILY
BLOCKED EMAIL " report send an email to ALL email accounts in your server .
The report contains a list of all email blocked for that account with
possibility to resend and whitelist. The report is sent each 24 hours .
You can exclude domain, users and email from this report.
The DAILY BLOCKED EMAIL should not be confused with the old (and
still active) "DAILY SPAM REPORTS" which is sent only to hosting
account owners email and it lists only the number of email blocked in
each owned domain name .
The DAILY BLOCKED EMAIL is useful for customers who does not check
for legitimate email in /spambox imap, spambox pop3 collector, ASSP Deluxe
cPanel log, asspblock@ reports .
Currently you can enable/disable the DAILY BLOCKED EMAIL only
globally using ASSP WHM interface > DAILY BLOCKED EMAIL .
In the future will be added cPanel frontend support, where customers will be
able to enable/disable this report using the ASSP Deluxe for cPanel
frontend.
DAILY BLOCKED EMAIL report customization
By default the report sent to your customers will
permit to resend and whitelist the email using the
WHITE link.
If you would only allow your customers to resend the email , without
whitelisting the sender, go to WHM > Automation settings and set OFF
autoAddResendToWhite ; now open ASSP Web
interface > Blocking report menu and set autoAddResendToWhite to
NO.
After this step the report sent your customer will permit only to
RESEND the blocked email .
Whitelist should be executed
later by customer using assp-white@ if required.
If you want customize the sender email , by default
spam_report@server_hostname , execute this
# echo "your_email" > /usr/local/assp/deluxe/daily_custom_email
# chmod 644 /usr/local/assp/deluxe/daily_custom_email
replace your_email with your custom email .
DAILY BLOCKED EMAIL ignore list
If you want reduce unnecessary SPAM from this list/report you
can use ccSpamNeverRe in your
ASSP GUI .
For example if you have a lot of
repetitive SPAM with subject "I want sell this
product to you" and you do not want see them
in your spambox and in your DAILY BLOCKED EMAIL
report you should add
I want sell this
product to you
in your
ccSpamNeverRe .
How to remove
Chinese SPAM in the Daily Blocked Email report ?
Sometime you may have tons of chinese SPAM in
your DAILY BLOCKED EMAIL report . If you want
avoid to see these chinese
SPAM in your
DAILY BLOCKED EMAIL simply execute this from
console
# touch /usr/local/assp/deluxe/no_chinese_spam_collection
# chmod 0644 /usr/local/assp/deluxe/no_chinese_spam_collection
after this step , the next DAILY BLOCKED EMAIL
report will be free from email with chinese
chars in the email subject.
In
ASSP Deluxe there is a useful tool which can be
run from console
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/find_abusers.php
It reports valuable information which permits you to understand in a fast way what kind
of email attack is receiving your server
, which are your accounts under heavy attack , which are bad ips attacking
your server (sorted) , if you have outgoing spam activity in your server.
Available commands
sw=n (or show=n
)
log=logfile
if you would
analyze a log different from current maillog.txt
The command sw=n shows you only data over the
number n . If you don't specify it, a value of 15 will be used.
example
# /usr/local/cpanel/3rdparty/bin/php-cgi /usr/local/assp/deluxe/find_abusers.php
sw=20
find_abusers.php will show following information
List of SPAM messages rejected by ASSP Scoring mode
List of SPAM messages rejected due to
"InvalidAddress" (dictionary attacks) (show domain destinations)
List of spam messages rejected due to "invalid
address rejected" (dictionary attacks) (show ip sender)
List of ips rejected by ASSP Scoring mode
List of ips rejected by relay attempt blocked
List of Local top senders list
List of Top spammers sending email dictionary
attacks
Top email subjects sent by spammers ( it creates a list
usable in bombSubjectRe /usr/local/assp/deluxe/bombSubjectRe.txt )
List of Top clamAV signatures
LIst of email sent from your server using a script
Using find_abusers.php as a cronjob
By default
ASSP installation you should
already have this cronjob .
( You can see your cron list in this way # crontab -e )
*/20 * * * *
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/find_abusers.php sw=39 rl=50 dc=40 on=1
above cronjob will collect all ips which are repetitively
attacking your server using
"email dictionary attack"
"assp scoring"
"relay attempt blocked"
Below is the recommend usage if you are using ASSP 1.x or
2.x (per installation you should already have this
cronjob)
*/20 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/find_abusers.php sw=29 rl=50 sc=30 dc=30
blockpb=yes on=1
where ...
dc= set the starting collection limit for "email dictionary attack"
sc= set the starting collection limit for
a "message
limit" (over total Scoring)
rl= set the starting collection limit for
"relay attempt blocked"
on=1 (or on=yes) =
required
if you want collect the ips and activate
blocking features .
sw=n (or show=n) any value below n will
not be processed ! .
If you don't specify show=n a default value of 15 will be assigned
 |
note: the sw= value should be always
lesser than any
value set. |
|
|
The cron above collects (each
20 minutes) in your /files/denysmtp.txt file
( denySMTPConnectionsFrom ** )
.
Using the cron above with values
sw=29 rl=50 sc=30 dc=40
on=1 ...
- > all ips which generated min. 50 (rl)
"relay attempt blocked" will be added in /files/denysmtp.txt file
(denySMTPConnectionsFrom) .
- > all ips which generated min. 40 (dc)
"invalid address errors" will be added in /files/denysmtp.txt file
(denySMTPConnectionsFrom) .
- > all ips which generated min. 30 (sc)
"ASSP Scoring blocks" will be added in /files/denysmtp.txt file
(denySMTPConnectionsFrom) .
note:
Ips which were found more than 70 times using dc= and sc=
checks, will be added in /files/blockip.txt instead of /files/denysmtp.txt
Other blocking features in find_abusers.php when
using on=1
When on=1 is added to your find_abusers.php cron ( by default
HOW TO you already have it ) find_abusers.php cron
will
also do the following task
|
Other blocking features in
find_abusers.php using on=1 |
When on=1 is added to your
find_abusers.php cron ( by default HOW
TO you already have it ) find_abusers.php cron will
also do the following task
- blockpb=yes
blockpb=yes added to your find_abusers.php cron will add in
/files/blockip.txt worst spammers ips (having a
PB score over 1000) .
- ips blocked due to SMTP
AUTHENTICATION errors (CSF addon) (
#fa01 )
find_abusers.php adds in your CSF firewall
deny list ( if you have installed and running CSF firewall ) all ips which are trying to force/hack an
smtp authentication
email . All entries greater or
equal to 60 ( smtpc=60 ) will be added to your CSF firewall
(deny list). It permits to block smtp authentication failures at early stage, reducing
password smtp brute force attacks. Ips which are listed in cfs.allow (csf whitelist)
or csf.ignore list
will not be added. The ip
will be added with a permanent block .
 |
DENY_IP_LIMIT value (CSF
firewall configuration) must be greater
than 2000. If DENY_IP_LIMIT is smaller
than 2000 ips will be added in
/usr/local/assp/files/blockip.txt ! |
|
|
If you would disable the feature add
smtpc=off
to your find_abuser.php cronjob . If you would customize the 60 value add
smtpc=n
where n could be greater (more moderate) or smaller (more
aggressive) than default value of 60 .
notice: Ips which are listed/added in cfs.allow
(csf whitelist)
will not be added in CSF deny list.
- ips blocked due to
invalidHeloRe errors (CSF addon)
(#fa02)
find_abusers.php adds in your CSF firewall
deny list ( if you have installed and running CSF firewall ) all ips which are
returning an error like this in your ASSP log .
Sep-20-18 01:06:47 [Worker_1] 216.250.125.27
info: found invalid helo 'ylmf-pc' - is immediatly blocked by
invalidHeloRe
All ips entries greater or
equal to 60 ( smtpc=60 ) will be added to your CSF firewall
(deny list). It permits to block invalidHeloRe failures at early stage. Ips which are listed in cfs.allow (csf whitelist)
will not be added.
If you would disable the feature add
helor=off
to your find_abuser.php cronjob . If you would customize the 60 value add
helor=n
where n could be greater (more moderate) or smaller (more
aggressive) than default value of 60 .
notice: Ips which are listed/added in cfs.allow
(csf whitelist)
will not be added in CSF deny list.
email addiction in blackdomains
email spammers which will be blocked over 50
times by the ASSP scoring filter will be added automatically in
ASSP web interface > validate sender > blackListedDomains
(/usr/local/assp/files/blackdomains.txt) .
You can customize the 50 value by adding blockthis=your_value
to your find_abusers.php cronjob .
for example if you would use blockthis=90
*/20 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/find_abusers.php sw=39 rl=50 dc=40
blockthis=90 on=1
If you would disable this feature you can use
blockthis=off
|
** By default collected ips will be added
in ASSP web interface > IP blocking >
denySMTPConnectionsFrom ( /usr/local/files/denysmtp.txt )
. denySMTPConnectionsFrom will block the ip
only after the email body and header checks .
If you would block the sender ip at early stage
before the email body and header checks execute this
touch /usr/local/assp/deluxe/extreme_yes
and the collected ips will be added to ASSP web
interface > IP blocking > denySMTPConnectionsFromAlways (
/usr/local/files/blockip.txt ) . If you would return to default ip
collection in denySMTPConnectionsFrom ( /usr/local/files/denysmtp.txt ) remove
the file /usr/local/assp/deluxe/extreme_yes ( # rm -f
/usr/local/assp/deluxe/extreme_yes )
How to allow a valid sender
If you think his ip has been collected by find_abusers.php
#denied
(i.e.
the sender receive a "service denied" bounced email )
1) put the email or domain which should pass in
ASSP WEB INTERFACE >
whitelisting menu > Whitelisted Domains and Addresses* (whiteListedDomains)
2) open your ASSP WHM and click "FLUSH IP BLOCKING"
The blocked sender should pass and he will not be blocked again in the
future.
OR
How to ignore ip address from collection
==> Using a
/usr/local/assp/files/ignore.txt
file
You can add the sender ip in this file
/usr/local/assp/files/ignore.txt and find_abusers.php will remove ips in
this list from /files/denysmtp.txt and /files/blockip.txt automatically.
for example
# echo "ip_address" >>
/usr/local/assp/files/ignore.txt
# /usr/local/cpanel/3rdparty/bin/php-cgi /usr/local/assp/deluxe/find_abusers.php
nodict exclusion file
Using a
/usr/local/assp/deluxe/nodict
file (70h)
If you want exclude from find_abusers.php bad ip collection for one or more domain names ,
simply put them (one by line) in /usr/local/assp/deluxe/nodict
. For example
if you have
gmail.com
yahoo.com
google.com
in your /usr/local/assp/deluxe/nodict file , no ip will be
collected for errors (email dictionary,spam scoring ..) for all email sent by
gmail.com,yahoo.com, and google.com .
How to make collections per domain
==> Using a
/usr/local/assp/deluxe/dmfile file
If you have 1 or more domain names under heavy email dictionary attack, you can
add all your domain names under heavy attack in the file
/usr/local/assp/deluxe/dmfile (one domain per line), then you can create a
new find_abusers.php like this
/usr/local/cpanel/3rdparty/bin/php-cgi /usr/local/assp/deluxe/find_abusers.php
show=5 dc=6 dm=file
on=1
find_abusers.php will process only domain names listed in file
/usr/local/assp/deluxe/dmfile
So for example you may
have this 2 cronjobs..
*/30 * * * *
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/find_abusers.php sw=39 rl=50 dc=40 on=1
*/20 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/find_abusers.php sw=5 dm=file dc=6 on=1
where the first
find_abusers.php is server wide , and it will create a failry moderate bad
ip collection , while the second find_abusers.php cron line will create an
aggressive bad collection ip using only domain names in
/usr/local/assp/deluxe/dmfile . So , /usr/local/assp/deluxe/dmfile
should contain a list of your most email dictionary attack bombarded domain names.
How to disable fully find_abusers.php collection ?
Set this simple cron (or replace current find_abusers.php cron)
without parameters as below,
*/20 * * * * /usr/local/cpanel/3rdparty/bin/php-cgi /usr/local/assp/deluxe/find_abusers.php
but do not remove the cron since it's used to detect outgoing spam activity
in your EXIM log ( more info ).
How to FLUSH blockip.txt and
denyalways.txt generated by find_abusers.php ?
Open your ASSP WHM and click FLUSH IP BLOCKING
You may also set a cron similar if you want flush your deny.txt and
blockip.txt each day .
0 1 * * 0,1,2,3,4,5 /bin/echo "" >
/usr/local/assp/files/denysmtp.txt
1 1 * * 0,1,2,3,4,5 /bin/echo "" > /usr/local/assp/files/blockip.txt
unexpected disconnection while reading SMTP command
If on EXIM maillog you see "unexpected disconnection while reading SMTP command"
lines without ACL errors , it's a normal behavior , ASSP is
disconnecting from EXIM because the email was rejected due to spam (email
dictionary attack or any other reason) .
I set up spambox ,do I need to manually make a folder in
everyone’s mailbox named “spambox” or will ASSP make the folder automatically as
needed? #spamb
spambox is an ASSP Deluxe plugin for ASSP and uses piping to redirect all
collected spam in customer /spambox imap fodler or in a
spambox@domain.com pop3 collector. The /spambox imap folder
appears automatically AFTER the first received spam in your imap
email client (thunderbird,outlook,the bat ...)
In Horde webmail it's shown immediately after the first received spa.
In Squirrel and and Roundcube, AFTER the first received spam the folder spambox
is subscribed automatically DAILY (each 24 hours) by ex_localdomains cronjob ;
OR your customer may subscribe the folder spambox manually (subscribe
folder in options) , in each case the spambox folder will be avaialable for
subscription after the first received spam.
Also , for customers which does not use webmail , or do not use imap , they can
collect all the spam in a pop3 spambox collector (spambox@domain.com).
Your customers can find detailed instruction (imap and pop3 spambox) in cPanel >
ASSP icon > SPAMBOX and cPanel > ASSP icon >
HELP
asspblock@ advanced usage
#block
If you or a customer would receive an email report with all the emal blocked
the email should be sent to asspblock@customerdomain.com
If you would know email blocked by user_a@customerdomain.com , you should send a
request to asspblock@customerdomain.com
from email user_a@customerdomain.com using an smtp authenticated request
(user_a@customerdomain.com smtp username and smtp password) .
As administrator using the ASSP web interface > blocking report menu,
you have other various options
as per help (description) included in ASSP web interface > blocking report >
Request Block Report (EmailBlockReport, default=assp-blockreport) and
in ASSP web interface > blocking report > File for Blockreportrequest (BlockReportFile)
For example you may setup ASSP to receive daily at your preferred hour
(BlockReportSchedule) the user_a@customerdomain.com asspblock report or
*@customerdomain.com (full domain report of all collected spam) assp block
report to any email (also external email like gmail i.e.) you prefer .
i.e. you can add this in File for Blockreportrequest (BlockReportFile)
*@customerdomain.com=> user_a@gmail.com
and user_a@gmail.com will receive daily a report of all email
blocked for customerdomain.com
How to downgrade from
ASSP v2 to ASSP v1
If you want roolback to ASSP v1 preserving
settings you should follow one of these two
procedures
- be sure all your ASSP Deluxe
is updated to latest version
- execute this
rm
-f /usr/local/assp/deluxe/upgrade2
- disable
MySQL using your ASSP WHM
- if you are using
Berkeley go to console and execute this
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/berk_off.php
- STOP
ASSP using your ASSP WHM
- open
/usr/local/assp/assp.pl with an editor and
replace
$version='2.4.4';
with
$version='1.9';
Save the file
- now
execute this
# rm -f
/usr/local/assp/deluxe/used_perl
# rm -fr
/usr/local/perls/
Now open ASSP WHM > go
down to ASSP update and execute an update to
ASSP v1 overwriting assp.cfg.
After the
update, update ASSP perl modules using your ASSP
WHM
finally set the cron
10 7 * * * cd
/usr/local/assp;perl
/usr/local/assp/rebuildspamdb.pl
All
should work correctly. If it does not work/start
install custom perl for your ASSP follow the
instructions in the
ASSP v1 HOW TO =>
www.grscripts.com/howto130.html , and
reinstall perl modules using your ASSP WHM.
OR you may follow this procedure to install
ASSP v1
- be sure all your ASSP Deluxe is
updated to latest version
- disable MySQL
using your ASSP WHM
- if you are using
Berkeley go to console and execute this
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/berk_off.php
- STOP
ASSP using your ASSP WHM
Now rename
/usr/local/assp in /usr/local/assp_old
Install ASSP v1 following the how to , copy from
/usr/local/assp_old to /usr/local/assp
all
files you need (spamdb, noprocessing list and so
on) .
Finally remove /usr/local/assp_old
How to setup email size limits in ASSP
[ #33j ]
 |
Max Size : it is the email
size of an email in bytes
Max Real Size : it is rcpt
size of the email message in bytes,
email size per number of email
recipients (rcpt)
What is local and remote ?
local email: an email sent FROM your
server from a local email . All email
which have a domain listed in
/etc/localdomains are considered local .
remote/external email : an email
sent from a remote server from an email
which is not in your server TO your
server |
|
|
|
Max email Size limits |
| -- ASSP Web interface >
SMTP session limits > Max Size of
Local Message Adresses (MaxSizeAdr) . Now you can set
individual maxSize values (email size limit in bytes) for
local email addresses,
domains, user names and IP addresses .
-- ASSP web interface > SMTP session limits
> Max Size of Incoming Message (maxSizeExternal) : You can specificy max
email size of an email coming from external.
By default it's set to 52428800 bytes (or 50 MB)
-- ASSP web interface > SMTP session limits
> Max Size of External Message Adresses (MaxSizeExternalAdr)
. Now you can set individual max Size values (email size
limit in bytes) for remote/external
email addresses, domains, user names and IP addresses .
-- ASSP web interface > SMTP session limits
> Max Size of Outgoing Message (maxSize) : You
can specificy max email size of an email sent
locally . By default it's set to 52428800 bytes (or
50 MB) |
|
Max email Real Size limits (email size per number of recipents) |
| -- ASSP Web interface >
SMTP session limits > Max Real Size
of Local Message Adresses* (MaxRealSizeAdr) . Now you can set
individual MaxRealSizeAdr values (email size limit in bytes
per number of recipients) for local
email addresses, domains, user names and IP addresses .
-- ASSP web interface > SMTP session limits
> Max Real Size of Incoming Message (maxRealSizeExternal) : You can
specificy Max real sizes (email size limit in bytes per number of
recipients) of an email coming from external.
By default it's set to 157286400 bytes (150MB)
-- ASSP web interface > SMTP session limits
> Max Real Size of External Message Adresses* (MaxRealSizeExternalAdr)
. Now you can set individual Max real sizes (email size limit in
bytes per number of recipients) for
remote/external email addresses, domains, user names and IP
addresses .
-- ASSP web interface > SMTP session limits
> Max Real Size of Outgoing Message (maxRealSize)
: You can specificy max real email size (email size limit in bytes
per number of recipients) of an email sent
locally . By default it's set to 52428800 bytes (or
50 MB) |
Is dovecot IMAP compatible with ASSP Deluxe ?
#j0
Yes , ASSP Deluxe is compatible with dovecot IMAP (available with
cPanel 11.24 and above)
Is NSD compatible with ASSP ? #h0
Yes , NSD is fully supported .
I would "no local address filter" enabled for all users but
hide it from the cpanel interface. How to do it ? #75
1) Only for some domain names
Suppose you want "no local" filter ENABLED for main domain , for example
domainx.com (and all its subdomains and parked/addon domain names), but
you would the filter "no local" fully HIDDEN on customer control panel you
should do this tweak ;
1) Open ASSP WHM , open ASSP DOMAIN CONFIG, select nolocal and be sure that
nolocal filter for domainx.com is ENABLED.
2) Open ASSP WHM , open ASSP DOM FILTER STATUS, select nolocal, and be sure
that nolocal filter for domainx.com is ENABLED.
3) Now go to console and execute this
echo "domainx.com_nolocal" >> /usr/local/assp/deluxe/per_domain_frontend_status
(of course replace domainx.com with the main domain of your client)
In case you would turn back , simply remove the line domainx.com_nolocal from
/usr/local/assp/deluxe/per_domain_frontend_status using an editor like
nano,vi ..
2) for all your accounts
simply
execute this
# touch
/usr/local/assp/deluxe/nolocal_hidden
# chmod 605 /usr/local/assp/deluxe/nolocal_hidden
no local filter will not be shown on cpanel frontend.
However you can control no_local filter status using ASSP WHM
To disable this feature and show again "no local"
filter on cpanel frontend simply
execute this
# rm -f
/usr/local/assp/deluxe/nolocal_hidden
how to use roundcube with ASSP
Deluxe ?
With cPanel 11.25 or above it should work automatically otherwise please read below.
If you would use ASSP email interface on Roundcube you should only
change in the roundcube conf file
/usr/local/cpanel/base/3rdparty/roundcube/config/config.inc.php following line
$rcmail_config['smtp_server'] = '';
with
$rcmail_config['smtp_server'] = 'localhost';
Then restart EXIM and ASSP. It will allow you to use the ASSP
Email interface (assp-spam@ assp-notspam@..)
Are the ASSP cpu and ram values shown in ASSP WHM
calculated in real time ?
NO, the values are calculated using "#
ps aux" which returns average values. If you would know the
real time values I recommend you to use this way instead of "top"
To get real time ASSP cpu usage in a single core or multicore server
( it read the ASSP cpu value for a time of 2 seconds for 3 times and returns the
average )
# pidstat -p assp_pid 2 3
To get real time ASSP memory usage in a single core or multicore server
( it read the ASSP memory value for a time of 2 seconds for 3 times and returns
the average )
# pidstat -r -p assp_pid
2 3
To get real time ASSP disk usage in a single core or multicore server
( it read the ASSP disk usage value for a time of 2 seconds for 3 times and returns
the average )
# pidstat -d -p assp_pid
2 3
if you are using "# top" and you have
a multi core server, be sure to click SHIFT+I to set Irix mode off
.
Note : the ASSP cpu charts in ASSP WHM
CHARTS are calculated using pidstat
How to add custom email/domain names to your assp_local_email
and assp_local_domains #820
If you want add custom domain names to your autogenerated
/deluxe/assp_local_domains , execute this
# nano /usr/local/assp/deluxe/custom_assp_local_domains
and add allowed local domain names , line by line .
If you want add custom email to your autogenerated /deluxe/assp_local_email ,
execute this
# nano /usr/local/assp/deluxe/custom_assp_local_email
and add allowed local email , line by line .
Automatic ASSP restarts to freeup
resources #819
ASSP Deluxe automatically safe restarts ASSP to free up resources ,
only if there are 3 ASSP connections (sup_lim) and if memory usage is over
150 MB.
To avoid multiple restarts this check will not apply again for 3 hours.
If you are using ASSP in "console mode" instead of daemon mode (default)
automatic restarts will be disabled.
If you would customize it, 4 options can be added to your update_email.php
cronjob as follow ;
=> raml=n to customize default 150 MB
=> fr=1 to force an ASSP restart even if there are more than 3 ( or
sup_lim ) ASSP
connections.
=> nofreeup=yes to disable this feature ( fully disable automatic restarts
in each situation )
=> sup_lim=n customize ASSP connections
spfdomainkey.php (install or uninstall spf
and DKIM for all your users) #840
With assp deluxe 5.2.4 and above a new script is avavilable , spfdomainkey.php
.
note : it requires cpanel 11.32 . If you have a version lower than cPanel
11.32 and ASSP deluxe lower than 5.2.4 dkey will install or uninstall
Domain Keys instead of DKIM .
It can be executed from console in this way
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/spfdomainkey.php
It permits to install or uninstall spf and DKIM for all your
domain names in your server. You can use following commands
SPF and domainkey installer/uninstaller
spf=on install spf for all users
spf=off uninstall spf for all users
dkey=on install DKIM for all users
dkey=off uninstall DKIM for all users
For example if you would install spf and DKIM for all your users
you should execute this
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/spfdomainkey.php spf=on dkey=on
How
to add a custom local ip address ? #841
note: following feature is available with ASSP Deluxe 3.7.0
and above .
BY default local ip addressed (which are allowed to send email in your server)
are automatically extracted by ASSP Deluxe using ex_localdomains.php cronjob .
If you want allow an ip which is not local you should follow this steps
Suppose you want allow ip address 134.120.120.134
Go to console and execute
nano /usr/local/assp/deluxe/custom_assp_local_ips
add the ip address 134.120.120.134 and
save the file.
Now execute
/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php
after this step the ip 134.120.120.134
should be listed in /usr/local/assp/deluxe/assp_local_ips
Now you should allow the ip in EXIM too . Open the file nano /etc/alwaysrelay
nano /etc/alwaysrelay
add the ip address 134.120.120.134 and
save the file.
Now restart antirelayd in this way
/scripts/restartsrv_tailwatchd
after this step the ip 134.120.120.134
should be listed in /etc/relayhosts .
Is there a way to block users from send email using "username@hostname" ? I find
that often spam are sent using this addresses and they actually don't exist.
(#A79)
by default these email are scored using
ASSP Web Interface => Validate sender > Check External Sender for Local
Address (DoNoValidLocalSender)
DoNoValidLocalSender will be scored by the value of flValencePB .
ASSP deluxe will set this value
1 point greater of your MessageScoringUpperLimit value to guarantee a block.
If you would customize flValencePB value execute this
echo "flValencePB" >>
/usr/local/assp/deluxe/no_auto_settings
Note : if the email are sent via
socket/sendmail they can't be checked by ASSP .
Why is ASSP blocking local senders ? .
(#A80)
If ASSP is blocking a local sender there is only one reason. He is not
sending email correctly , so ASSP is treating him such as remote sender .
Since ASSP applies all SPAM filters to remoter senders , if the client send
email using his isp (i.e.)
ASSP will consider the local user such a remote sender, and the email could be
blocked (often the isp ips
are blacklisted on RBLs or have some misconfiguration).
To solve the problem simply invite the client to send email correctly using
smtp mail.clientdomain.com
in this way ASSP will recognize him such as localsender and ASSP will never
block him , on the countrary
each email sent by the client will contribute to automatic ASSP whitelisting
If the customer set an smtp which is not local , ASSP will treat him such as a
remote sender and his email will be filtered and could be blocked too. ASSP
never blocks a local sender if the local sender send email correctly using smtp
mail.hisdomain.com or any other valid smtp in the server . If the local user
send email correctly can also use the ASSP email interface commands (assp-white,
assp-spam ..other) , can take advantage of automatic whitelist each time he send
an email , can take advantage of personal
blacklist each time he reports (forward as attachment) a spam (assp-spam@) , can receive a list of
blocked email (using asspblock@) .
On the countrary if he send email incorrectly he will be treated such as any
other remote sender and will be filtered.
how to edit the deluxe/relayhosts file ?
deluxe/relayhosts get ips dinamically from antirelayd cPanel ; these are ips
which are smtp authenticated (these ips can't be removed) or ips listed in
/etc/alwaysrelay (these can be removed by editing /etc/alwaysrelay ) .
If you want add some ips which need to relay please follow this
http://www.grscripts.com/howtofaq.html#841
Which are ASSP parameters controlled by ASSP Deluxe ?
#custom
Various ASSP parameters are controlled/modified automatically by ASSP Deluxe
, if you want
customize them open your
ASSP WHM and click AUTOMATION SETTINGS. You can see a list of these parameters
and you can turn off them if you would preserve your custom settings .
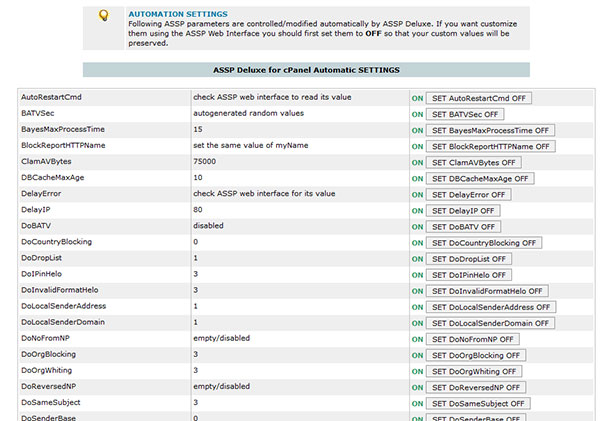
I'm now receiving a lof of LOCALHOSTRELAY emails from CSF /
lfd . (#A82)
It's a normal behavior( ASSP communicates with EXIM via 127.0.0.1 ) ; to fix
this "problem" open the csf web interface , go to "Edit lfd ignore file" ,
select RT_Localrelay , click "edit" and enter 127.0.0.1 . Save Settings.
How to fix /etc/remotedomains and /etc/localdomains
( obsolete in newer cPanel !)
. (#A87)
With ASSP Deluxe 3.7.5 and above ex_localdomains.php can fix your
/etc/remotedomains and /etc/localdomains lists (moving correctly remote domains
to /etc/remotedomains and local domains to /etc/localdomains ).
If you would run this feature you should add lc=1 to your
ex_localdomains.php in this way (execute the command from console)
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php lc=1
you can also add the option show=1 (execute the command from console)
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php lc=1 show=1
if you want see the output .
does clamd needs to
be activated
(enabled) on the
service manager in
order to work with
ASSP ?
.
(#A85)
YES .
clamd works with
ASSP to block
email viruses and
malware and if you use the
unofficial clamd
signatures script
http://www.grscripts.com/tweaking.html#8
it can also block
much more spam.
ASSP Deluxe for cPanel ASSP outgoing activity notifications
using EXIM log
#2IK
ASSP Deluxe for cPanel (Deluxe version 10.0.8 and above) using the
ex_localdomains.php cronjob, checks each 3 hours email queue size
and local SMTP authenticated senders, and send you an email warning if the
condition below are matched. If you receives an email like this there could be
some huge email outgoing activity (legitimate or illegitimate/spam), so you
should check what's happening in ASSP/EXIM logs and take actions as
needed/required (change pop3 email password i.e.) .
Conditions
The email warning will be sent IF your email queue is bigger than
5 (qu=queue)
and
IF you have a local sender(s) which sent more than
250 email (top=email value) analyzing latest
12 hours (check_hours=hours)
of your EXIM log ( /var/log/exim_mainlog ) .
The email will be sent to the email contact you have set on your ASSP WHM and
in your WHM > Basic cPanel & WHM Setup and/or
you can specify an alternative email ( cex=youremail
).
You can customize the qu
,
check_hours,
cex and top
values
by editing the file
nano /usr/local/assp/deluxe/email_warnings
If you would ignore some email included in the top local sender email warning you should add them in this
list (one email per row)
nano /usr/local/assp/deluxe/warning_ignore
You can stop these email notifications executing this from console
# touch /usr/local/assp/deluxe/stop_queue
or/and re-enable them by executing this from console
# rm -f /usr/local/assp/deluxe/stop_queue
note : the usage of analyze_this
in /email_warnings is deprecated, you can now use
check_hours
(i.e. check_hours=6) as explained above.
note : number of email sent under 25 ( email sent in latest check_hours
hours ) will not be shown in the email report .
note : if the email report is sent and after three hours
the email report will be similar, it will not be sent again
note : for testing purpouses
you can send the email report even if conditions are not satisfied in this way
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/ex_localdomains.php gonow=1
ASSP Deluxe for cPanel EXIM same email subject outgoing notifications
#23K
ASSP Deluxe for cPanel (Deluxe version 10.0.8 and above) using the
ex_localdomains.php cronjob, checks your
EXIM log ( /var/log/exim_mainlog ) each 3
hours
and send you an email warning if the
condition below are matched.
The email warning will be sent
IF you have more than 25 (
limit_top=25 ) email having the "same
email subject" sent (using SMTP dovecot authentication or by a script) in
the latest 12 hours ( check_hours=hours )
.
Data is extracted from your EXIM log ( /var/log/exim_mainlog ) .
If the latest email warning will not change for 5 consecutive times ,
the email will not be resent, even if the conditions are matched.
The email will be sent to the email contact you have set on your ASSP WHM and
in your WHM > Basic cPanel & WHM Setup and/or
you can specify an alternative email ( cex=youremail
).
You can customize the
limit_top,
check_hours,
and cex
by editing the file
nano /usr/local/assp/deluxe/email_warnings
If you would ignore some email subject in your notifications you should add them in this
list (one email per line)
nano /usr/local/assp/deluxe/ignore_subject
How to use the information provided in the warning
if you receive a warning like this
1452 = > T="Someone you follow is sex"
129 = > T="!EMPTY SUBJECT!"
21 = > T="RENTAL VEHICLE BOOKING REQUEST"
21 = > T="Re: Anatolien kilim"
note the first row , 1452 email sent using the email subject "Someone you
follow is sex" . The value is fairly large, this
could be an incoming spam or outgoing spam message; this should be investigated
for example in the way described below.
1 - grep the subject in ASSP log (you may use grep -m5 to limit results to 5)
grep "Someone you follow is sex" /usr/local/assp/maillog.txt
2- grep the subject in EXIM log too (you may use grep -m5 to limit results to 5)
grep "Someone you follow is sex" /var/log/exim_mainlog
Once you find the row in the logs, grep some EXIM email ID (i.e.
1W9VJj-001Vvx-GB ) in EXIM log and some ASSP email ID (i.e. id-39124-01337) in
ASSP log and try to read the email content.
i.e. you may find the email content in ASSP WHM > EXIM QUEUE or also in ASSP
log
If you verify that the email sent are SPAM,
You should check if the email was sent using an SMTP authenticated email ( in
this case change email password ) or using
a script ( you should have a cwd=/home/user/public_html row in your EXIM log
this case ). If using a script you should check the script vulnerability in the
user account to stop the outgoing activity.
Need help ? : if you need support you may order
this service
for an investigation of your outgoing activity ; support does not include fix of
script vulnerabilities.
EXIM queue commands
Some useful exim queue command which could be useful if your server exim queue
is huge
Deliver all messages in email queue
except of frozen messages
exim -qf
Deliver all messages in email queue included frozen
messages
exim -qff
View the body of the message
exim -Mvb msgid
View the header of the message
exim -Mvh msgid
Number of email in Queue:
# exim -bpc
Queue overview
# exim -bp | exiqsumm
msg-ids in queue
# exiqgrep -i
Search sender messages in queue
# exiqgrep -f [sender]@domain.tld
Search recipient messages in queue
# exiqgrep -r [sender]@domain.tld
Search messages in queue, based on age (older than 24 hours)
# exiqgrep -o 86400
Search messages in queue, based on age (younger than 24 hours)
# exiqgrep -y 86400
Remove all frozen messages in queue:
# exiqgrep -z -i | xargs exim -Mrm
Remove old queued messages, for example older than
24 hours:
# exiqgrep -o 86400 -i | xargs exim -Mrm
Remove messages matching sting in body :
# grep -lr 'string to match'
/var/spool/exim/input/ | sed -e 's/^.*\/\([a-zA-Z0-9-]*\)-[DH]$/\1/g' | xargs
exim -Mrm
Remove all messages in queue
# grep -lr '' /var/spool/exim/input/ | sed -e
's/^.*\/\([a-zA-Z0-9-]*\)-[DH]$/\1/g' | grep -v "spool" | xargs exim -Mrm
antispam software
is it possible to disable spambox collection for a single
LOCAL email ? #9f
yes if you are using ASSP Deluxe 4.5.5 or above.
Go to console SSH and execute this
# nano /usr/local/assp/deluxe/skip_spam_for
enter the local email (line by line, each line 1 email) which should
bypass/skip spambox collection. Save the file.
is it possible to disable spambox collection for a REMOTE
DOMAIN ?
yes if you are using ASSP Deluxe 9.6.2 or above.
Go to console SSH and execute this
# nano /usr/local/assp/deluxe/skip_spam_for
enter the remote domain(s) (line by line, each line 1 domain) which should
bypass/skip spambox collection. Save the file.
ASSP Deluxe and ASSP WHM automatic updates
#2KK
Since ASSP WHM version 5.8.0 and ASSP Deluxe 4.2.0 , you can
automatically update ASSP WHM and ASSP Deluxe for cPanel .
Simply open your ASSP WHM interface and be sure you have AUTOMATIC UPDATES
enabled for ASSP WHM and ASSP Deluxe like the image below ;
Your ASSP WHM or ASSP Deluxe version will be checked each 24 hours
using ex_localdomains.php cronjob.
If a new version will be detected your ASSP WHM and/or ASSP Deluxe will be
updated automatically.
You will receive an email notification . The email will be sent to the
email contact you have set on your ASSP WHM .
If you want set a custom email you should add
cex=custom@email to your ex_localdomains.php cronjob .
You can stop this email notification executing this from console
# touch /usr/local/assp/deluxe/stop_update_notification
and re-enable executing this from console
# rm -f /usr/local/assp/deluxe/stop_update_notification
How to remove from /usr/local/assp/whitelist flat file all
email older than n days ?
#7JK
or ... How to remove
from /usr/local/assp/whitelist flat file email added in latest n days ?
Note : if you have MySQL or BerkeleyDB already running
do not execute this. The commands below are valid if you are
running ASSP with flat files (MySQL or BerkeleyDB not running). I recommend to
execute the commands below with ASSP stopped.
You should use clean_whitelist.php from console. This script creates a
/usr/local/assp/whitelist smaller removing older entries.
If you want remove
email withelist older than 200 days (e.g.) execute this
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/clean_whitelist.php date=200
If you want remove only email withelist added
in the last 10 days (e.g.) execute this
# /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/clean_whitelist.php date=10 new=yes
A copy of your old /usr/local/assp/whitelist will be created in
/usr/local/assp/whitelist_backup
I'm having issues with @gmail and others importants emails
being blocked because:
X-Assp-Spam-Reason: counter (16) for domain 'bol.com.br' surpassed
DomainBoxLimit (15) #12n
Open assp web interface and put @gmail.com in Validate Senders
> Don't do Blacklisted for these Addresses and Domains* (noBlackDomain)
If the domain is not so important like gmail.com the customer can whitelist it
using assp-white@ or you as admin can add it in Whitelist menu > Whitedomains
If you do not want penalize domain senders you can also disable
noBlackdomain, using Validate sender menu >
DoDomainBox , set it to Disabled. Or you can increase the block
from 15 (default) to some value greater (DomainBoxLimit).
I would restart ASSP each day at 00:15 , how to do ?
#13n
you may set a cron which stop and start ASSP rocess at 00:15
0 15 * * * /usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/stop.php;/usr/local/cpanel/3rdparty/bin/php-cgi
/usr/local/assp/deluxe/start.php
ASSP professional anti-spam software
How to reset HMM and Bayesian DB in ASSP v2 ?
#res_db
if you want reset your HMM and Bayesian Databases in your ASSP v2 you may
follow these steps :
- Open the ASSP WHM interface and STOP ASSP.
- Delete files /usr/local/assp/spamdb and
/usr/local/assp/HMMdb
rm -f /usr/local/assp/spamdb
rm -f /usr/local/assp/HMMdb
- Open your ASSP MySQL db using phpmyadmin
(there is a link in your ASSP WHM > MYSQL
SETUP) and click "empty"
in the hmmdb and spamdb rows .
- remove all files contained in
/usr/local/assp/mysql/dbimport
rm -f /usr/local/assp/mysql/dbimport/*
- Open the ASSP WHM interface and
START ASSP .
- Execute a "Rebuild SPAM
DB" . After about 15 minutes you should have
a new and working HMM and Bayes db


















